Roger Clarke’s Identity Home-Page
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke’s Identity Home-Page© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
This segment of the site provides access to papers that I've published in the broad area of 'Identity'. Included within the scope is the concept of 'Entity'; the processes of Identification (of identities) and Entification (of entities); and both the Identifiers that distinguish each instance of an identity, and the Entifiers that distinguish each instance of an entity. Additional concepts that are addressed include Nymity and Nyms, and its sub-categories of Pseudonyms and Anonyms.
Building on that foundation, a critique of the inadequacies of conventional 'identity management' is provided, together with a replacement framework that I call '(Id)Entity Management', encompassing Identification and Entification, Authentication, Authorisation and Access Control, and extending to many further topics, such as Identity Silos, very importantly the Digital Persona, and Cyborgisation.
The terms in bold are not mainstream. I coined them in order to have words that expressly refer to important concepts overlooked by the vast majority of people working in these areas. Because of this massive blind spot, conventional models used in information systems fail to properly reflect the world, resulting in significant design deficiencies. Some progress has been made, with over 1500 Google citations of the suite of publications.
The resources in this segment of the site can be accessed in the following ways, most useful first:
The Topic-Based Index of my papers on identity themes, up-to-date at 31 December 2023, below
The What's New Page (because the indexes are never fully up-to-date), here
The Chronological Index of my papers on identity themes, here
The Search Facility, in the button at the top-right-hand side of the page
See also the following recent and comprehensive papers:
I undertook consultancy and research on what the industry refers to as 'identity management' for about 30 years mid-1990s to mid-2020s. I spent the last 20 years of that period explaining that the undertaking embodied fundamental misconceptions.
I eventually found the time to produce a series of papers that explains the reasoning from the ground up, and proposes an alternative that I call '(Id)Entity Management'.
An Overview provides background and a brief summary of the seven substantive papers:
The terminology and definitions are brought together in a Glossary.
An earlier rendition of the model is in 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' (2010), supported by Application of the Model (2010).
Glossaries of the terms and their definitions were provided here:
An even earlier, and succinct, summary of the model is provided in 'Identification and Authentication Fundamentals' (2004).
Critiques of mainstream theory and practice are in:
The mature model built on many papers and presentations, including:
I've published on this only briefly, primarily in the early sections of 'Human Identification in Information Systems' (1994). I really should summarise key references from the humanities and social science literatures some time.
An Entity is a real-world thing (a pallet, a computer, an animal, a human being). An Identity is also a real-world thing, but is of virtual rather than physical form. Commonly it is a presentation of an entity. Entities may have many identities, reflecting their diverse roles in different contexts.
This sub-topic has been central to my work in the area, because it is foundational, and the conventional blurring of the two concepts has caused enormous problems for eBusiness and eGovernment.
The most accessible of the analyses I've undertaken are in:
Nymity is a characteristic of an Identity, whereby it cannot be associated with any particular Entity.
The foundation analysis is in 'Human Identification in Information Systems' (1994), and was expanded in:
The analysis was consolidated in:
And the analysis is embodied in 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' (2009-10).
The concept of 'PETs' dates to 1995. An explanation is in:
The ideas were developed in a series of papers:
This sub-topic is concerned with records and data-items, and their relationships to (id)entities and their attributes.
The foundation work is the paper on 'Human Identification in Information Systems' (1994)
See also 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' (2009-10)
This sub-topic also encompasses the notion of 'data silos'
I introduced this concept in 'Computer Matching and Digital Identity' (1993)
The key work is 'The Digital Persona and Its Application to Data Surveillance' (1994)
I reviewed progress in 'Promise Unfulfilled: The Digital Persona Concept, Two Decades Later' (2012)
I applied it in Risks Inherent in the Digital Surveillance Economy: A Research Agenda (2019)
See also 'Human-Artefact Hybridisation and the Digital Persona' (2005)
An (Id)entifier is a data-item or items that enable the (Id)entity to be distinguished from others in the same category.
(Id)entification is the process whereby data is associated with a particular (Id)entity. This is achieved by acquiring an (Id)entifier for it.
This area of my work builds on the fundamental notions of Identity and Entity, and applies the extended model to the ways in which organisations associate data with real-world (Id)entities. It thereby lays the foundation for understanding the serious deficiencies in conventional approaches to 'identity management'.
The foundation work is the paper on 'Human Identification in Information Systems' (1994)
See also 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' (2009-10)
And see A Reconsideration of the Foundations of Identity Management, and slide-set (Bled, 2022)
This sub-topic also encompasses the notion of 'identity silos'
A Nym is an Identifier whose association with an underlying Entity is not known.
See the references in 3.1 Nymity, above.
See also 'Famous Nyms' (2000).
Data about individuals is claimed to (and sometimes does) contain potential value for purposes other than dealings with the particular individual. Individuals' data privacy has been severely compromised by organisations that expropriate and then exploit data for extraneous purposes.
It might be feasible to enable additional uses, without harming privacy, if the data can be manipulated in some way, in order to break the association of the data with a particular person. One way to do this is to aggregate, i.e. to suppress individual records but to release summary data, so that the details apply to multiple people rather than one. Another is to 'de-identify' or 'anonymise' each record.
Unfortunately, removal of obvious identifiers is not enough, and nor are the various forms of 'data perturbation' that have been proposed, experimented with and even trialled. Rich data-sets are essentially impossible to effectively de-identify. Techniques are available, and more keep appearing, that enable organisations to re-identify records that were supposedly anonymous, i.e. to re-associate them with the relevant individual.
A 2019 paper, entitled 'Beyond De-Identification: Record Falsification to Disarm Expropriated Data-Sets', surveys the area, shows that existing de-identification techniques are simply inadequate and will remain so, and proposes two approaches that can work: the generation of synthetic data, and Known Irreversible Record Falsification (KIRF).
Authentication is the process whereby a level of confidence in an assertion is achieved. One (of many) forms is '(id)entity authentication', which is a process to achieve some level of confidence in an assertion that an (id)entifier is being appropriately used. Conventional approaches to identity management fail to distinguish between the authentication of entity and of identity, resulting in flaws in most schemes that are seriously detrimental and in some cases fatal.
This sub-topic also encompasses the notions of verification, tokens, authenticators, credentials, evidence of identity and proof of identity.
The foundation work is the paper on 'Human Identification in Information Systems' (1994)
A comprehensive analysis is in 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' (2009-10)
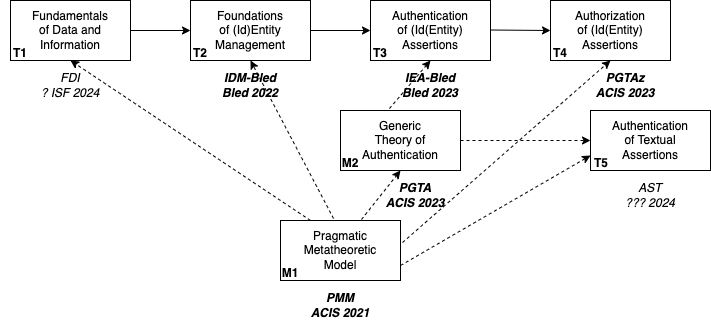
A restatement is in process, building on 'A Platform for a Pragmatic Metatheoretic Model for Information Systems Practice and Research' (2021). This comprises:
Important steps in the development of the ideas are in these papers:
Other relevant publications include:
Additional publications of relevance are listed under the sub-topics below.
Credit-card-sized plastic is the most common of a number of forms that can be used as tokens (i.e. means of carrying an identifier such as a customer-code in a form that is easily captured) or as credentials (i.e. means of carrying information that assists in authenticating an assertion, most commonly an identity assertion. For example, the card may carry a copy of the person's signature).
The term 'ID card' is very loosely used to refer to cards that are used both as tokens and as credentials. An ID card can be used for a very specific purpose, for multiple-purposes, or for general-purposes. There is always a tendency for a narrow-purpose ID card to drift towards wider purposes. The sub-topics below deal with the specifics. The following papers have addressed the general topic of cards:
A comprehensive scheme to enable identification and identity authentication of a population is usefully referred to as a national identification scheme. An ID Card is one element among many in such a scheme. A number of papers have addressed the topic.
The primary papers are:
Other resources include:
During the 1970s and 1980s, an application of cryptography emerged that promised to enable the authentication of message-senders. A sender could append a block of text to a message, which was encrypted in such a way that the recipient could be confident that only the purported sender could possibly have generated it. The block of text was called (somewhat misleadingly) a 'digital signature', and the paraphernalia needed to support the mechanism was called 'public key infrastructure' (PKI).
The mathematics is wonderful, but unfortunately the idea as a whole is extremely difficult to implement effectively. The primary papers in which I analysed the problems and proposed solutions are:
The following papers examined particular aspects of the topic:
Biometric technologies endeavour to identify people, or to authenticate assertions about people, based on some physical characteristic that is, or is asserted or assumed to be, reliably unique. Most biometrics technologies don't work effectively in the real world. A very few – essentially only fingerprints and iris (and, in narrowly constrained contexts, hand geometry) – have any credibility. But even these have a vast array of quality and security problems. Despite this, business and government keep trying to implement biometric schemes.
Whether they are effective or not, biometric technologies are extraordinarily threatening to freedoms of the individual. My papers have summarised the nature of biometrics, and examined the wide range of myths that have been perpetrated and sustained by biometrics suppliers, their industry associations, and national security and law enforcement agencies.
The most important papers are:
Other papers and presentations include:
A number of papers have directly addressed the question of the use of cards containing micro-chips as a means of implementing tokens (to assist in human identification) and/or credentials (to assist in human identity or entity authentication):
A major use of (id)entification and (id)entity authentication by organisations is to control access to 'system resources' (i.e. software and data). An authenticated identity is allowed access on the basis of previously-decided authorizations (sometimes also called permissions and privileges). The process as a whole is often referred to by information security specialists as 'access control'.
The many presentations of conventional models and terminologies in these areas are highly inconsistent and confusing. I've been working on fixes for the problems since the late 1990s.
The model as a whole is presented in section 1 above, a fuller overview paper, and a Glossary
The paper most directly-relevant paper in the series is Access Control in the Era of Active Artefacts: A Generic Theory of Authorization to Support IS Practice and Research (2023)
An earlier version is 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' (2009-10)
Other papers of relevance include:
This sub-topic also encompasses the notions of user, loginid/userid/username, account, registration, pre-authentication, enrolment, single sign-on, and simplified sign-on.
Identity Management is a generic term for architectures, infrastructure and processes that support the authentication of assertions relating to identity, and the authorisation of access to system resources.
The area has been a muddle of technological, standards and competitive activity since the late 1990s. It will continue to be a muddle, because the majority of schemes, when evaluated against the model put forward in my work, fail dismally.
I refer to my proposal as (Id)Entity Managememt (IdEM). The model is presented in section 1 above, a fuller overview paper, and a Glossary
The paper most directly-relevant paper in the series is Access Control in the Era of Active Artefacts: A Generic Theory of Authorization to Support IS Practice and Research (2023)
An earlier version is 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' (2009-10)
The most important papers are:
Other papers and presentations include:
(Id)entification and (Id)entity authentication are enablers of many things. One of them is finding people, and recording their successive locations, in order to support retrospective or (increasingly) real-time surveillance.
The major papers in this area are:
Other papers include:
My analyses of the many aspects of human identity in the information era are generally pregnant with policy concerns and policy implications.
The most important papers in which the policy aspects predominate are as follows:
Other papers include:
I have published only a limited amount in the way of prognostications about the future of identity, and much of that is brief, and embedded in a scatter of papers. One specific aspect is outlined in a final sub-section below. The following text provides a brief indication of why I judge that next half-century is looking decidely unattractive.
During the second and third decades of the 21st century, a range of factors will conspire to threaten the fragile civil freedoms enjoyed in 2000 by residents of the more economically-advanced nations. The political power of the brigade of the self-righteous, who wish to impose their values on everyone else, will be strengthened by social turmoil arising from such factors as:
Law and order lobbyists and their allies in technology-providing corporations, aided by the corporatised, for-profit nation-states emergent from contemporary 'public-private partnerships', will make repeated attempts to impose authoritarian technologies and mechanisms, including:
Under such circumstances, the scope for free speech, and especially for opposition to authoritarian measures of the kinds listed above, will be much more constrained. Given the dramatic and entirely unjustified authoritarian legislation passed in most 'free' countries between 2002 and 2007 on the pretext that it was necessary in the 'war against terrorism', there is a significant prospect that freedoms associated with human identity may be insufficiently protected by political will, and may depend for their survival on technological failures, economics and institutional collapse.
Humans are increasingly being fitted and implanted with prostheses (which recover lost functionality) and orthoses (which provide additional functionality). Meanwhile, robots are slowly increasing in their capabilities. If both of these transpire to be trends rather than short-term phenomena, then the notion of human, and with it human identity, will progressively change.
A short, simple statement is in 'Cyborgs Today' (2017), an interview for National Radio News
I began my investigations of emergent reality in this area by means of 'Asimov's Laws of Robotics: Implications for Information Technology' (1993-94).
A more substantial investigation was in
These predicted Oscar Pistorius knocking on the door of Olympic competition in 2008 – as it turned out, correctly.
The impacts on human identity were the subject of a preliminary analysis in 'Human-Artefact Hybridisation and the Digital Persona' (2005).
See also 'Hybridity - Elements of a Theory' (2005).
Some years later, I examined Cyborg Rights (2011) (final version in IEEE Technology & Society).
I also considered aspects of the drone phenomenon that involve cyborgism in What Drones Inherit from Their Ancestors (Computer Law & Security Review, June 2014).
More generally, see Homo Roboticus and Roboticus Sapiens.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 24 February 2009 - Last Amended: 31 December 2023 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/ID/index.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy