Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Principal, Xamax Consultancy Pty Ltd, Canberra
Visiting Fellow, Department of Computer Science, Australian National University
Version published in Proc. Conf. ECIS'2001, Bled, Slovenia, 27-29 June 2001
Version of 3 May 2001
© Xamax Consultancy Pty Ltd, 2001
This document is at http://www.rogerclarke.com/II/ECIS2001.html
The fuller Working Paper from which it is drawn is at http://www.rogerclarke.com/II/PKIMisFit.html
It has been conventional wisdom that, for e-commerce to fulfil its potential, each party to a transaction must be confident about the identity of the others. Digital signature technology, based on public key cryptography, has been claimed as appropriate means to achieve this aim. Digital signatures do little, however, unless a substantial 'public key infrastructure' (PKI) is in place, such that parties know what is being authenticated, and what level of assurance is provided.
Conventional PKI, built around the ISO standard X.509, has been, and will continue to be, a substantial failure. This paper examines conventional X.509v3-based PKI architecture, and identifies key deficiencies including its inherently hierarchical and authoritarian nature, its unreasonable presumptions about the security of private keys, a range of other technical and implementation defects, confusions about what it is that a certificate actually provides assurance about, and its inherent privacy-invasiveness. A model is presented that explains the naiveté of identity authentication, and how e-commerce needs to be baaed on `nyms` rather than `identifiers`. Alternatives to conventional PKI are identified.
There has been a popular perception that the adoption of e-commerce has been significantly slowed because, in cyberspace, buyers don't trust unidentifiable sellers. Digital signatures, and the mechanism that supports them, Public Key Infrastructure (PKI), have been touted as the solution to the problem. Despite well over a decade of development, however, very limited progress has been made, and each step forward with PKI seems to create a set of new sub-problems.
Meanwhile, a range of other impediments to net-consumer trust of cyberspace merchants has been identified (Clarke 1999c), and PKI has been criticised on both technical grounds (e.g. Davis 1996, Ellison and Schneier 2000, Schneier 2000), privacy grounds (e.g. Greenleaf & Clarke 1997) and commercial effectiveness (e.g. Winn 2001). This paper consolidates the critiques of PKI, with the intention of working towards digital authentication mechanisms that are more attuned to what the Information Society really needs.
The paper commences by stating the trust problem as it was originally perceived, and describing the currently conventional technology that has been applied in an endeavour to solve it. Major problems with that solution are then identified, in the areas of its hierarchical nature, insecurity of the private key, technical and implementation deficiencies, its failure to provide useful assurances to net-users, and its privacy-invasiveness. The paper concludes with an explanation of the critical nature of 'nyms', and a brisk assessment of alternative approaches to achieving trust which offer better prospects for meeting the real needs of the Information Society.
The commercial potential of the Internet became apparent only in the mid-1990s. Wired Magazine, launched in October 1994, claimed that its Hotwired venture was the first commercial web-site (Clarke 1999c), although Pizza Hut has also staked a claim to that mantle (Hobbes 1990-).
From an early stage, the conventional wisdom was that e-commerce, in comparison with purchasing in a physical location like a shop, lacks the important comfort factors of seeing who you're dealing with, or at least being able to see the merchant's physical 'foot-print', and check the physical attributes of the value being transferred. It was therefore postulated that successful commerce on public networks would be dependent on some other means of establishing trust.
A leap was then made to the conclusion that trust would need to be based on a mechanism for the identification of parties who deal on the net, supplemented by authentication mechanisms to test the assertions of identity. A recent expression of this is that "Fundamentally, electronic commerce involves the use of remote communications and therefore necessitates all parties involved to authenticate one another ... [because] the parties will not at the time of transacting have face to face dialogue" (McCullagh A. & Caelli, 2000).
Moreover, the demand for identity was presumed to be two-sided, i.e. not only would the merchant or service-provider identify themselves to the consumer but consumers would also identify themselves to sellers. It is unclear whether this was a conscious assumption, and if so whether it was based on an analysis of merchant behaviour, or was merely a pretext for the creation of exploitable trails of consumer behaviour. Either way, it represents a significant compromise to the freedom of consumers who have hitherto conducted most of their purchases anonymously.
This section provides a brief overview of the key technologies that have enabled engineers to address the perceived problem described above.
During the 1980s, public key (or 'asymmetric') cryptography had emerged. Public key cryptography involves two related keys, referred to as a 'key-pair', one of which only the owner needs to know (the 'private key') and the other which anyone can know (the 'public key'). Because only one party needs to know the private key, it does not need to be transmitted between parties, and hence it need never be exposed to the risk of interception. Knowledge of the public key by a third party, on the other hand, does not compromise the security of message transmissions (Diffie & Hellman 1976, Schneier 1996). For a tutorial treatment, see Clarke (1996), and for a short history see Ellison, in RFC2963 (1999).
The following sub-sections introduce firstly the application of public key cryptography to 'digital signatures', and then the infrastructure on which they depend. The dominant standard is then outlined and interpreted.
Digital signatures are a particular application of public key cryptography. A digital signature is a block of data that is generated from a message prior to its despatch, and is appended to it. The block is prepared by a two-step process:
The recipient re-creates the message digest from the message that they receive, uses the sender's public key to decrypt the digital signature that they received appended to the message itself, and compares the two results. If they are identical, then, so cryptographers argue:
This paper concerns itself with only the second of these, the use of a digital signature to authenticate something about the message-sender.
Digital signatures were naively presumed by many people to provide unqualified assurance. In practice, however, the effectiveness of the mechanism is dependent on a number of conditions, in particular:
As this paper explains, those conditions are generally not fulfilled by conventional PKI.
Digital signature schemes depend on the public key of the message-sender being available to the recipient. The most practicable methods of achieving this are:
All of these approaches are subject to 'spoofing', i.e. an imposter can send a message that includes a public key, or store a public key in a readily accessible directory, and thereby fool the other party into thinking the message came from a particular person or organisation.
To address this risk, the concept was created of a 'certificate' that attests to the fact that the particular public key is associated with a particular party. (The technical literature uses the term 'is bound to' rather than 'is associated with'. Many readers would infer from that term a far stronger form of association than the technique actually warrants).
More precisely, a 'certificate' is a digitally signed, structured message that asserts an association between specific data and a particular public key. An 'identity certificate' is then a particular class of certificate that associates a particular identifier with a particular public key. (It will be argued later in this paper that the term 'identifier' should really be replaced by 'nym'). Regrettably, most of the literature uses the term 'certificate' ambiguously, to refer to both certificates generally and identity certificates in particular, despite the fact that the differences are extremely important.
According to conventional thinking, a certificate needs to be created by a trusted 'public key certification authority' (CA). A CA digitally signs each certificate using its own private key. In most schemes, the certificate is provided to the party that claims the particular key to be its own. That party then includes it in the messages that they send. A message with a CA's certificate attached therefore functions in a manner analogous to a letter applying for a job being accompanied by a letter from a referee attesting to something about the applicant, such as their identity, their good character, their experience, or their qualifications.
A CA needs to undertake some form of authentication process in order to satisfy itself that the claimed association actually exists. A conventional approach is to depend on the services of a Registration Authority (RA), such as a Post Office. A comprehensive process would require the person with whom the key is to be associated to undertake all of the following:
Such procedures are highly inconvenient, intrusive and expensive, and the load falls on the individuals who are required by organisations to participate. As a result of the costs and difficulties, all existing schemes make very significant concessions to practicality, and thereby undermine their integrity.
The security of private keys is vital to the whole process, but is capable of being compromised. When, not if, a private key is compromised, the certificate must be revoked very quickly. An efficient and effective mechanism is therefore required to record and provide access to revocations of certificates and the associated key-pairs.
The dominant standard used at present as the foundation for PKI is the family of CCITT X.500 standards, in particular X.509 (X.509 1988, 1997, and Housley et al. 1999). The current version of X.509 is number 3, usually referred to as X.509v3, which was finalised in 1997. A set of standards, dubbed PKIX, enables use of X.509 approaches within the web-context (W3C 2000). Guidance has been provided by texts such as Ford & Baum (1997), Adams & Lloyd (1999) and Austin (2000).
Ellison (1997) describes the history this way: "the X.500 proposal was published [in the late 1980s]. It was to be a global directory of named entities. To tie a public key to some node or sub-directory of that structure, the X.509 certificate was defined. The Subject of such a certificate was a path name indicating a node in the X.500 database - a so-called 'Distinguished Name'. The X.500 dream has effectively died but the X.509 certificate has lived on. The distinguished name took the place of a person's name and the certificate was called an 'identity certificate', assumed to bind an identity to a public key ...". In short, X.509 was the hammer that came to hand when the nail was discovered.
All forms of PKI necessarily involve some degree of intrusiveness, in order that sufficient quality can be achieved. Conventional PKI, built around X.509v3 certificates, is especially severe. Implementations commonly have many of the following features:
Current X.509v3 certificates go so far as to permit an agent of an organisation to protect their personal identity through the use of a role-title, but they actually preclude an individual (referred to as a 'residential person') from having that capability. Moreover, some implementations may preclude a residential person from possessing multiple personal key-pairs, even though the same person is permitted to possess multiple key-pairs for organisations that they represent.
Some schemes involve the key-pair generation process being compulsorily performed by some organisation on behalf of individuals, and perhaps even compulsory storage of the private key for the benefit of parties other than the individual concerned (commonly referred to as 'escrow').
X.509v3 certificates provide a limited means for communicating attributes, within the primary certificate or through the creation of secondary certificates which may attest to one or more characteristics of the individual. But the attributes are inherently linked to and dependent on the primary certificate, which bears the individual's identifier. Hence anonymity and even pseudonymity are still precluded.
The issuing of notice that a key-pair and certificate(s) have been revoked is supported by an inefficient download mechanism called Certificate Revocation Lists (CRLs - X509, 1988, 1997 and Housley et al. 1999). A more recent specification for an on-request look-up is Online Certificate Status Protocol (OCSP - Myers et al. 1999).
This paper uses the terms `conventional PKI` and `X.509-based PKI` to refer to public key infrastructure based on X.509v3 certificates, including its Internet variant, PKIX.
This section presents a catalogue of problems with X.509-based PKI.
X.509-based PKI is inherently hierarchical. This is because trust in the CA is not automatic, and each layer of CAs needs to be attested to by some superior layer. Conventional PKI therefore depends on a third party that is partly but not entirely trusted, which in turns depends on another such partly but not entirely trusted third party, which needs to be attested to by some further superior layer. This results in an unholy spiral up to some mythical authority in which everyone is assumed to have ultimate trust. Trust in the real world has never worked like that, and trust in cyberspace won't either.
Such schemes can also be readily argued to be authoritarian in nature (Clarke 1994b). For example, there is an intrinsic assumption that every party that acquires a certificate is required to disclose their identity, even if the only functional need is to communicate eligibility (e.g. their age, qualifications, or agency relationship with a principal). RAs have considerable power, to the extent that they are able to deny a person a digital identity.
X.509-based PKI makes the assumption that the 'distinguished name' has to be unique within the 'name-space'. This precludes the second and subsequent individuals who seek to use a particular name (Clarke 2000b) from using their own name without some kind of qualifier. It also provides no basis for individuals to use alternative identifiers, and implicitly denies individuals the capability to have and use multiple key-pairs, and multiple certificates. The engineers who created the X.509 standard appear to have been blithely unaware that multiple identities per person are entirely legal in many jurisdictions, particularly those whose legal systems derive from that of the United Kingdom (Clarke 1994c).
Underlying digital signatures and PKI is the assumption that the holder of a private key will be able to ensure its security. During the 1999-2000 period, corporate servers have been subject to a rash of electronic break-ins. The ease with which many of these `hacks` have been performed has demonstrated the serious inadequacy of the precautions taken by organisations of all kinds and all sizes. Standards have been issued by governments (e.g. TCSEC 1985, ITSEC 1991, Common Criteria 1998), and guidance provided by text-books (e.g. Garfinkel & Spafford 1997), but the degree to which organisations have applied the principles and guidance is embarrassingly low.
Conventional PKI also assumes that consumers and citizens will have, and will need to use, private keys. There are many ways in which malicious software (malware) can be applied to discover, copy or invoke private keys, in memory or on disk. The hardware and systems software of commodity workstations, particularly mainstream Windows and MacOS machines, currently provide very little in the way of security features. Moreover, few products are available that enable consumers to graft such security features on to their work-and-play facilities, and such products as exist require considerable expertise to install and configure (Kaiser 2000). Private keys on 'commodity workstations' that are connected to the Internet via commercial Internet Access Providers therefore remain highly susceptible to a wide array of risks, both of capture, and of invocation without the authority of, or even knowledge of, the consumer/citizen.
A range of problems have been identified with the technical design of X.509-based PKI and with its implementation in real-world applications (Ellison & Schneier 2000). These include problems with the assumption that a single global name-space exists, the difficulty of detecting that a private key has been subject to compromise, many difficulties in implementing an effective revocation process, and the onerousness and demeaning nature of registration processes.
Even where solutions exist, they are commonly ignored or flouted. Hierarchical schemes are undermined by reliance on 'self-signed' certificates by CAs, i.e. blind trust by other parties in the CA, its intentions, and its procedures. Most schemes fail to implement effective revocation procedures, using either the CRL or OCSP specifications. The major implementations of X.509-based PKI, such as that based on the Verisign certificates embedded in commercially-available web-browsers, are at best 'relaxed' applications of formal X.509 standards, and hence the current PKI is even less meaningful than that which would be feasible if it was applied as intended. CAs find it necessary to deflect attention from the critical weaknesses of their services by drawing attention to the physical and electronic security of the facilities that they use to generate the certificate.
In addition to all this, the X.509 standards are long, rich, complex and imprecise, with the result that interpretations of the standard are required, and many variants, commonly termed 'profiles', exist (see, for example, Gutmann 2000). Commercial applications are clumsy to implement, and considerable difficulties and delays are experienced, even by skilled technicians, in relation to the generation of keys, the acquisition of certificates, and the management of certificates. All schemes compromise the theoretical requirements, and thereby undermine their purpose.
A critical feature of PKI schemes is the warranties and indemnities provided by the CA to accompany the assurance. It would be expected that the CA would incur financial liability if the assurance that the sender was who the sender purported to be transpires to be incorrect, and a party's reasonable dependence on the assurance results in economic cost. The wording provided by web-browsers suggests considerable protection, e.g. "The signer of the Certificate promises you that the holder of this Certificate is who they say they are" (Macintosh Netscape Navigator 4.08).
Such bold assurances are, however, subject to a great deal of qualification. CAs commonly describe their procedures for associating persons with online identities in 'Certification Practice Statements', and express the commercial aspects in 'Certificate Policy Statements'. These are often phrased in ways that obscure rather than clarify. Moreover, "The certification authority may establish different classes of certificates with different prices and different degrees of scrutiny applied in reviewing the application" (Winn 1998), and the conditions are generally phrased so that they minimise the CA`s exposure to liabilities.
In any case, the concept of 'authentication' has been seriously misunderstood by the designers of X.509-based PKI. Authentication is a process whereby a degree of confidence is established in the truth of an assertion. There are many kinds of assertions that can be the subject of authentication processes. Among them are assertions of the form 'this artefact has a value equivalent to so much of a particular currency', and 'the sender of this message has a credential that attests to their having a particular attribute, or their eligibility to perform a particular function'.
In order to discuss the real meaning of a certificate, some definitions of terms are needed:
The kind of assertion that certificates are supposed to provide assurance about is 'the sender of this message is the entity that uses a particular identifier'. A certificate does not, however, attest to that. What it does attest to is that:
Depending on the registration process that was applied, a certificate may also attest that:
A certificate provides no assurance, however, about whether:
Moreover, such assurance as a certificate provides is qualified by the terms of the CA's Certificate Policy Statement, as dictated by the CA's lawyers; and very limited recourse is available should the assurance be wrong. A relying party appears to have little or no legal protection, not just if the CA was wrong, but even if the CA was negligent (e.g. Sneddon 2000).
The previous sections have focussed mainly on technical inadequacies, but mentioned privacy in passing. Greenleaf & Clarke (1997) considered the privacy impact of conventional digital signatures and PKI. That paper categorised the wide range of threats into those involving private keys (variously during generation, storage and backup, escrow, access and revocation), and risks arising in relation to public keys (including identification requirements, registers and revocation logs). In addition, there are consequential implications such as further increases in expectations of identification, imposition of requirements to carry a token such as chip-card, and the gross privacy imposition of biometrics as a security mechanism for the private key.
Some of these problems are features of conventional PKI schemes that could be avoided or designed around. Many, however, are direct implications of the nature of the X.509 architecture and certificate design.
Conventional PKI involves enormous complexity, effort and expense, in return for insecure protections, very weak evidence, and very limited recourse. Both corporations and individuals, including consumers, citizens, employees and contractors (especially those in sensitive circumstances) should have serious doubts about schemes of this nature being inflicted upon them.
The previous section argued that PKI's impacts on individuals are severe. If e-trust schemes are to serve the needs of the Information Society, the focus must be moved away from identities of individuals, and mechanisms must be at least tolerant, and even actively supportive, of anonymity and pseudonymity (Clarke 1993, 1994 and 1999). Application of these concepts is critical to ensure that the advent of cyberspace does not mean the death of private space.
The following related needs exist:
These objectives can be achieved through the application of the concept of a 'nym'. This is the pseudo-identity that arises from anonymous and pseudonymous dealings (McCullagh D. 1996-, Clarke 1999b).
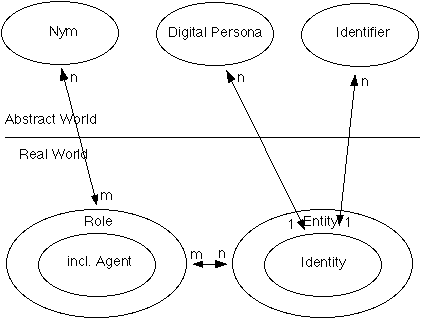
An earlier section offered definitions for the terms 'entity', 'identity', 'digital persona', and 'identifier'. Three further terms require explanation:
This gives rise to the web of concepts depicted in Exhibit 1.
Nyms are not mere imagination: technologies exist that enable them. See EPIC (1997-) and Clarke (1999a). Moreover, it is critical to the future of e-commerce that the information infrastructure supports nyms, and that people adjust to their existence and nature. As Ellison (1997) argued: "The [U.S. House Hearing] asked 'Do you know who you are doing business with?'. Before answering that question, one should really answer the two questions: 'Do you need to know who you are doing business with?', and 'Can you know who you are doing business with?'".
Nyms are in practice replacing identifiers. Services and protocols such as IRC, MUDDs and ICQ expressly support them. So do several of the alternatives to conventional PKI that are discussed below. Any approach to inculcating trust in marketspaces will need to implement persistent nyms at least for the consumer side of transactions.
Conventional PKI are ineffectual and privacy-invasive. Fortunately, there are other ways to address the need for trust in marketspaces. Their discovery depends in part on re-definition of the problem. This section briefly scans some alternative approaches that may provide better fit to the needs of the Information Society.
The 'web of trust' approach is intrinsic to the longstanding alternative product Pretty Good Privacy (PGP) - (Zimmerman 1995, Garfinkel 1995, Bacard 1995, Stallings 1995). This avoids the need for professional CAs, because certificates can be issued by anyone. Fault-tolerance is achieved by depending on multiple certificates, probably with varying weightings assigned to them by the evaluator, on the basis of the degree of trust they place in the person who provided the certificate. PGP supports nyms. It depends on email-addresses, which are unique, because of the manner in which domain-names are allocated, and aliases and user-names are assigned. They are not formally linked to entities, however, and may have any of a 1:1 relationship with a single person, or 1:n (multiple people may share the same address), or n:1 (a person may have multiple addresses); or indeed m:n (multiple accounts may be used by multiple people). The practicality of PGP's specific implementation of the 'web of trust' notion has been criticised, but arguments have been pursued for the concept to be broadened and applied more generally (Grossman 2000).
Another standardisation process is that which grew out of Simple Public Key Infrastructure (SPKI) - (Ellison 1996, IETF 1997-, Wang 1998, Ellison 2000). The momentum has now shifted to a parallel initiative, the Simple Distributed Security Infrastructure (SDSI) - (Rivest & Lampson 1996, SDSI 1996, Ellison 2000), into whose current version SPKI features have been incorporated. The two approaches are in the process of being harmonised. The key element of SDSI is that the X.509 nirvana of a single, global name-space has been abandoned. With it, the presumption has been removed that 'name' (or, better expressed, 'identifier') is reliably bound to a particular entity. The certificate associates a public key (and hence a key-pair) to an entity that only the CA knows, and no warranties are provided to the recipient of the message by the CA as to who the keyholder is. It is up to the relying party to build up an image of the sender based on its successive interactions with the holder of that key. Attributes are associated with public keys, not with identities of real-world entities.. SPKI/SDSI supports nyms, because no identifier is reliably associable with a particular entity, and each entity may use multiple key-pairs.
Brands (2000) proposes a different conception and implementation of digital certificates, such that privacy is protected without sacrificing security. The validity of such certificates and their contents can be checked, but the identity of the certificate-holder cannot be extracted, and different actions by the same person cannot be linked. Certificate holders have control over what information is disclosed, and to whom. If they prove to be implementable, Brandsian certificates will be expressly anonymous.
Trust may be based on reputation, by which is meant 'generally held' positive opinion about an entity. There are several ways in which 'generally held' opinion can arise, including reputation based on experience, performance, or social networks. Marketing specialists have substituted image for substance, and manufactured proxies for reputation. An entity can use advertising and public relations techniques to establish or embellish a brand name, which it protects using the particular form of intellectual property law called trademarks. An entity can seek to engender trust in itself by using someone else's brand, such as a seal of approval from an organisation that projects advertising and public relations on behalf of its clients. I refer to such arrangements as `meta-brands` (Clarke 2001).
An approach that avoids and dissolves the problems with PKI rather than trying to solve them, is trust-management systems (Blaze 1999, Blaze et al. 1999a, Blaze et al. 1999b). These can be viewed as generalisations of longstanding access control techniques for achieving security of software processes and data. The trust management approach also offers ways of addressing privacy. This is because it focusses primarily on privileges and restrictions rather than the identification of individuals, and hence it can deal with nyms representing pseudonymous roles just as readily as with names that are associated with an identified entity.
The originally perceived need was that, for e-commerce to become mainstream, merchants needed to identify themselves, and to enable authentication of the identifiers they provided. Marketers sought schemes in which consumers also needed to identify themselves to the seller. This paper has cast grave doubt on the need for identification and authentication, particularly of consumers. It has drawn attention to the manifold failures of conventional PKI to deliver on its claims, and to its seriously privacy-invasive nature.
There remain a few contexts in which digital signatures can be effective. In particular, it can be applied internally by organisations that have structures that are strictly hierarchical and relatively stable. National defence agencies, and some kinds of large corporations, are arguably of that kind. In addition, a related approach can be applied on Extranets that link defined and bounded communities of organisations and individuals. Where the participants are well-known to one another from prior dealings, a scheme can be devised to leverage off the existing relationships in order to associate a key with a particular community-member. Winn (1998) refers to these as 'closed-bound communities'. Note that, in such circumstances, the conventional PKI is essentially irrelevant (Wheeler 1998, Wheeler & Wheeler 1998).
The technical orientation that has been adopted by the proponents of conventional, X.509-based PKI does not address the needs of the Information Society. The real requirement is for trust in e-interactions: consumers want security and convenience, but without surrendering personal data to sellers (and to others who may gain access to it, e.g. other merchants and government agencies).
Conventional PKI suffers very serious inadequacies. The existence of an increasingly rich set of alternatives shows that the time has now come to recognise the inherent deficiencies of X.509 architectures, and abandon attempts to impose them on open, public systems.
Adams C. & Lloyd S. (1999) 'Understanding the Public-Key Infrastructure' New Riders Publishing, 1999
Austin T. (2000) `PKI : A Wiley Tech Brief` Wiley, 2000
Bacard A. (1995) 'The Computer Privacy Handbook: A Practical Guide to E-Mail Encryption, Data Protection, and PGP Privacy Software', Peachpit Press 1995, at http://www.andrebacard.com/press.html
Blaze M. (1999) 'Using the KeyNote Trust Management System', November 1999, at http://www.crypto.com/trustmgt/kn.html
Blaze M., Feigenbaum J., Ioannidis J. & Keromytis A. (1999a) 'The KeyNote Trust-Management System Version 2' RFC2704, IETF, September 1999, at http://www.crypto.com/papers/rfc2704.txt
Blaze M., Feigenbaum J., Ioannidis J. & Keromytis A. (1999b) 'The Role of Trust Management in Distributed System Security' Chapter in Vitek & Jensen (Eds.) 'Secure Internet Programming: Security Issues for Mobile and Distributed Objects, Springer-Verlag, 1999, at http://www.crypto.com/papers/trustmgt.pdf
Branchaud, M. (1997) 'A Survey of Public Key Infrastructures', Master's Thesis, Department of Computer Science, McGill University, Montreal, March 1997, at http://www.xcert.com/~marcnarc/PKI/thesis/
Brands S.A. (2000) 'Rethinking Public Key Infrastructures and Digital Certificates: Building in Privacy' MIT Press, 2000
Clarke R. (1993) 'Computer Matching and Digital Identity' Proc. Computers, Freedom & Privacy, February 1993, at http://www.rogerclarke.com/DV/CFP93.html
Clarke R. (1994a) 'The Digital Persona and its Application to Data Surveillance' The Information Society 10,2 (June 1994), at http://www.rogerclarke.com/DV/DigPersona.html
Clarke R. (1994b) 'Information Technology: Weapon of Authoritarianism or Tool of Democracy?' Proc. World Congress, Int'l Fed. of Info. Processing, Hamburg, September 1994. At http://www.rogerclarke.com/DV/PaperAuthism.html
Clarke R. (1994c) 'Human Identification in Information Systems: Management Challenges and Public Policy Issues' Info. Technology & People 7,4 (December 1994). At http://www.rogerclarke.com/DV/HumanID.html
Clarke R. (1996) 'Cryptography in Plain Text', Privacy Law & Policy Reporter 3, 2 (May 1996) 24-27, 30-33, at http://www.rogerclarke.com/II/CryptoSecy.html
Clarke R. (1997) 'Chip-Based ID: Promise and Peril' Proc. Int'l Conf. on Privacy, Montreal, 23-26 September 1997, at http://www.rogerclarke.com/DV/IDCards97.html
Clarke R. (1998) 'Public Key Infrastructure: Position Statement', May 1998, at http://www.rogerclarke.com/DV/PKIPosn.html
Clarke R. (1999a) 'Privacy-Enhancing and Privacy-Sympathetic Technologies: Resources', April 1999, at http://www.rogerclarke.com/DV/PEPST.html
Clarke R. (1999b) 'Identified, Anonymous and Pseudonymous Transactions: The Spectrum of Choice' Proc. User Identification & Privacy Protection Conf., Stockholm, 14-15 June 1999, at http://www.rogerclarke.com/DV/UIPP99.html
Clarke R. (1999c) 'The Willingness of Net-Consumers to Pay: A Lack-of-Progress Report', Proc. 12th International Bled EC Conf., Slovenia, June 1999, at http://www.rogerclarke.com/EC/WillPay.html
Clarke R. (2000a) 'Privacy Requirements of Public Key Infrastructure' Internet Law Bulletin 3, 1 (April 2000) 2-6. Republished in 'Global Electronic Commerce', published by the World Markets Research Centre in collaboration with the UN/ECE's e-Commerce Forum on 'Electronic Commerce for Transition Economies in the Digital Age', 19-20 June 2000, at http://www.rogerclarke.com/DV/PKI2000.html
Clarke R. (2000b) 'Famous Nyms', June 2000, at http://www.rogerclarke.com/DV/FamousNyms.html
Clarke R. (2000c) 'Interview', September 2000, at http://www.rogerclarke.com/DV/BiometixIview.html
Clarke R. (2001) 'Meta-Brands` Privacy Law & Policy Reporter 7, 11 (May 2001), at http://www.rogerclarke.com/DV/MetaBrands.html
Common Criteria (1998) 'Common Criteria for Information Technology Security Evaluation', Common Criteria Implementation Board, Version 2, 1998, at http://www.cse.dnd.ca/cse/english/cc2dwnld.html
Corcoran D., Sims D. & Hillhouse B. (1999) 'Smart Cards and Biometrics: Your Key to PKI', Linux Journall (March 1999), at http://www2.linuxjournal.com/lj-issues/issue59/3013.html
Davis D. (1996) `Compliance Defects in Public-Key Cryptography` Proc. 6th Usenix Security Symp., San Jose CA, 1996, pp.171-178, at http://world.std.com/~dtd/compliance/compliance.pdf
Diffie W. & Hellman M. (1976) 'New directions in cryptography' IEEE Transactions on Information Theory, pp. 644-654, November 1976
Ellison C. (1996) 'Establishing Identity Without Certification Authorities', Proc. 6th USENIX Security Symposium, San Jose CA, July 22-25, 1996, at http://world.std.com/~cme/usenix.html
Ellison C. (1997) 'What do you need to know about the person with whom you are doing business?' Written testimony of Carl M. Ellison to the U.S. House of Representatives Science and Technology Subcommittee, Hearing of 28 October 1997: Signatures in a Digital Age, at http://world.std.com/~cme/html/congress1.html
Ellison C. (1999) 'The nature of a usable PKI' Computer Networks 31 (1999) 823-830
Ellison C. (2000a) 'Naming and Certificates', Proc. Computers, Freedom & Privacy 2000, at http://www.cfp2000.org/papers/ellison.pdf
Ellison C. (2000b) 'SPKI/SDSI and the Web of Trust' September 2000, at http://world.std.com/~cme/html/web.html
Ellison C. & Schneier B. (2000a) 'Risks of PKI: Electronic Commerce' Inside Risks 116, Commun. ACM 43, 2 (February 2000), at http://www.counterpane.com/insiderisks5.html
Ellison C. & Schneier B. (2000b) 'Ten Risks of PKI: What You're Not Being Told About Public Key Infrastructure' Computer Security Journal, v 16, n 1, 2000, pp. 1-7, at http://www.counterpane.com/pki-risks.html
EPIC (1997-) 'EPIC Online Guide to Practical Privacy Tools', at http://www.epic.org/privacy/tools.html
Ford W. & Baum M.S. (1997) 'Secure Electronic Commerce: Building the Infrastructure for Digital Signatures and Encryption', Prentice Hall, 1997
Froomkin A.M. (1996) 'The Essential Role of Trusted Third Parties in Electronic Commerce' Oregon L. Rev. 75,1 (Spring, 1996) 49-115
Garfinkel S. (1995) 'PGP: Pretty Good Privacy' O'Reilly & Associates, 1995, at http://www.ora.com/catalog/pgp/
Garfinkel S. & Spafford G. (1997) 'Web Security & Commerce' O'Reilly, 1997
Gerck E. (1998) 'Overview of Certification Systems: X.509, CA, PGP and SKIP', August 1998, at http://www.mcg.org.br/cert.htm
Gerck E. (2000) 'Overview of Certification Systems: X.509, CA, PGP and SKIP', July 2000, at http://www.mcg.org.br/certover.pdf
Greenleaf G.W. & Clarke R. (1997) `Privacy Implications of Digital Signatures', IBC Conference on Digital Signatures, Sydney (March 1997), at http://www.rogerclarke.com/DV/DigSig.html
Grossman W. (2000) 'Circles of Trust', Scientific American, August 2000, at http://www.sciam.com/2000/0800issue/0800cyber.html
Gutmann P. (2000) 'X.509 Style Guide', at http://www.cs.auckland.ac.nz/~pgut001/pubs/x509guide.txt
Hobbes R. (1990-) 'Hobbes' Internet Timeline v5.1', at http://info.isoc.org/guest/zakon/Internet/History/HIT.html
Housley R., Ford W., Polk W. and Solo D. (1999) 'Internet X.509 Public Key Infrastructure Certificate and CRL Profile', RFC 2459, January 1999, at http://www.ietf.org/rfc/rfc2459.txt
IETF (1997-) 'Simple Public Key Infrastructure (SPKI)', at http://www.ietf.org/html.charters/spki-charter.html
ITSEC (1991) 'Information Technology Security Evaluation Criteria', Version 1.2, Commission of the European Communities, June 1991, http://www.itsec.gov.uk/docs/
Kaiser T. (2000) 'Secure Storage of Private Keys on Commodity Workstations', Unpublished Honours Thesis, Department of Computer Science, Australian National University, November 2000
Khare R. & Rifkin A. (1997) 'Weaving a Web of Trust' Revised version of a paper World Wide Web Journal 2 3 (Summer 1997) 77-112, at http://www.cs.caltech.edu/~adam/local/trust.html
Kohnfelder, L. M. (1978) 'Towards a Practical Public-key Cryptosystem' MIT S.B. Thesis, May 1978
Lampson B., Abadi M., Burrows M. & Wobber E. (1992) 'Authentication in distributed systems: theory and practice' ACM Transactions on Computer Systems, 10(4):265-310, November 1992, at http://gatekeeper.dec.com/pub/DEC/SRC/research-reports/abstracts/src-rr-083.html
Lundblade L (1997) 'A Review of E-mail Security Standards' Proc. Conf. INET'97, at http://www.isoc.org/inet97/proceedings/A4/A4_1.HTM
McCullagh A. & Caelli W. (2000) 'Non-Repudiation in the Digital Environment' First Monday 5, 8 (August 2000), at http://firstmonday.org/issues/issue5_8/mccullagh/index.html
McCullagh D. (1996-) 'Nym', at http://www.well.com/user/declan/nym/
Myers M., Ankney R., Malpani A., Galperin S. & Adams C. (1999) 'X.509 Internet Public Key Infrastructure: Online Certificate Status Protocol - OCSP', IETF RFC2560, June 1999, at http://www.ietf.org/rfc/rfc2560.txt
RFC2692 (1999) 'SPKI Requirements' Internet Engineering Task Force of The Internet Society, September 1999, at ftp://ftp.isi.edu/in-notes/rfc2692.txt
RFC2693 (1999) 'SPKI Certificate Theory' Internet Engineering Task Force of The Internet Society, September 1999, at ftp://ftp.isi.edu/in-notes/rfc2693.txt
Rivest R.L. & Lampson B. (1996) 'SDSI - A Simple Distributed Security Infrastructure', 15 Sep 1996, at http://theory.lcs.mit.edu/~rivest/sdsi10.html
Schneier B. (1996) 'Applied Cryptography' Wiley, 2nd Ed., 1996
Schneier B. (2000) 'Why Digital Signatures Are Not Signatures` Crypto-Gram 15 November 2000, at http://www.counterpane.com/crypto-gram-0011.html
SDSI (1996-) 'A Simple Distributed Security Infrastructure (SDSI)', 1996-, at http://theory.lcs.mit.edu/~cis/sdsi.html
Sneddon M. (2000) ,Legal Liability and e-Transactions` National Electronic Authentication Council, Canberra, Australia, August 2000, at http://www.noie.gov.au/publications/NOIE/NEAC/publication_utz1508.pdf
Stallings W. (1995) 'Protect Your Privacy: The PGP User's Guide' Prentice Hall, 1995
TCSEC (1985) 'Trusted Computer System Evaluation Criteria', U.S. Department of Defense, at http://www.radium.ncsc.mil/tpep/library/rainbow/5200.28-STD.html
W3C (2000) 'Public-Key Infrastructure (X.509) (pkix)', at http://www.ietf.org/html.charters/pkix-charter.html
Wang Y. (1998) 'SPKI' December 1998, at http://www.hut.fi/~yuwang/publications/SPKI/SPKI.html
Wheeler L. (1998) 'Account Authority Digital Signature Model (AADS)', at http://www.garlic.com/~lynn/aadsover.htm
Wheeler A. & Wheeler L. (1998) 'PKI Account Authority Digital Signature Infrastructure', November 1998, at http://www.garlic.com/~lynn/draft-wheeler-ipki-aads-01.txt
Winn J.K. (1998) 'Open Systems, Free Markets,and Regulation of Internet Commerce' 72 Tulane L. Rev. 1177 (1998), at http://www.smu.edu/~jwinn/esig.html
Winn J.K. (2001) ,The Emperor's New Clothes: The Shocking Truth About Ditial Signatures and Internet Commerce` forthcoming, Idaho Law Review, 2001, at http://www.smu.edu/~jwinn/shocking-truth.htm
X.509 (1988, 1997) 'The Directory - Authentication Framework', Volume VIII of CCITT Blue Book, pages 48-81, CCITT/ITU, 1988, 1997
Zimmermann P.R. (1995) 'PGP 5.0 User's Guide' MIT Press, 1995, at http://mitpress.mit.edu/book-home.tcl?isbn=0262740176
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 3 May 2001 - Last Amended: 3 May 2001 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/II/ECIS2001.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy