Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Preliminary Draft of 13 March 2023
© Xamax Consultancy Pty Ltd, 2021-23
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://rogerclarke.com/ID/IEA.html
The practice of IS, particularly in the context of identity management activities, does not adequately reflect uncomfortable but important realities about identities and the entities that underlie them. An analysis is presented of assertions commonly relied upon by business processes, and of the means whereby those assertions can be authenticated. This is based on a previously-published pragmatic metatheoretical model, and a generic study of the concept of authentication. The analysis has material implications for the practice of IS, and for IS researchers whose work is intended to influence IS practice.
Organisations have encountered ongoing difficulties in the areas of identification and authentication, particularly where the entities in question are human beings. The topic of identity authentication is addressed in the technical information technology (IT) literature, although far less so in information systems (IS). On the other hand, authentication as a general concept and a family of business processes has attracted remarkably little attention. For example, of the 465 refereed papers from the Bled eConference accessible in the AIS electronic Library (AISeL), covering the last two decades, only 2 have the term 'authentication' in Title or Abstract. In AISeL as a whole, the corresponding count is only 38 of >17,000, and across the Basket of 8 IS journals, a mere 12 of >10,000 articles. These primary sources were complemented by more open-ended searches across the Google Scholar catchment, and in several journals whose domains of interest made them appear likely prospects to contain relevant articles. All of the papers found by searching for the term in full-text were inspected, but this identified only about two dozen that contribute significantly to the analysis reported in the present paper. I contend that suitable designs depend on a much better appreciation by IS designers of the nature of the phenomena that they seek to document and to control, and that this warrants for more attention from researchers.
To deliver better understanding and better designs, IS professionals need to be supported by a model that is pragmatic, by which is meant that it is a fit to the needs of IS practitioners, and that reflects insights from relevant aspects of philosophy. This paper builds on prior work that presents analyses of the relevant phenomena reflected in a pragmatic metatheoretic model, and of the general concept of authentication. Application of that model provides the basis for an analysis of authentication processes for assertions about identity.
The paper commences with a recapitulation of prior work that established a pragmatic metatheoretic model. It then draws on current work on the generic concept of authentication of assertions. The main body of the paper identifies specific categories of assertion in which identities and/or entities play a key role. Processes are then discussed whereby the reliability of those kinds of assertions can be assessed. The effectiveness of those processes is shown to be dependent on evidence, and hence on the quality of the data on which reliance is placed. The application of these ideas to IS practice is argued to enable improvements in authentication design and operation. The need is shown for further work on their application to particular kinds of entities and identities.
Organised activity involves dependence by parties on statements made by other parties. The longstanding maxim 'Trust, but verify'conveys that, in principle, all such statements on which dependence is placed need to be checked, but with effort invested proportionately to the harm that would arise from unjustified trust. Organisations need IS to be designed in a manner that reflects, supports and facilitates the checking of important statements. For that to be achieved, the model on which IS practice is founded needs to have an effective fit with the manner in which business enterprises, government agencies, not-for-profits and small businesses perceive the realities of their operational environment.
The first sub-section below summarises a model that is pragmatic, in that it supports understanding about and action in the world, yet has a firm foundation in relevant aspects of meta-theory, particularly ontology (the study of existence), epistemology (the study of knowledge), and axiology (the study of values). The second sub-section introduces a further area of prior work which examines the general notion of authentication. On these two foundations, the remainder of the paper builds an analysis of the authentication of assertions that involve identities and entities.
Prior work reported in Clarke (2021) presents a pragmatic metatheoretic model conceived in order to support both IS practice and that portion of IS research activity that is intended to be relevant to IS practice. The sense in which the term 'an IS' is used is consistent with that proposed by Avison & Fitzgerald (2006): "a system which assembles, stores, processes and delivers information ... a human activity (social) system which may or may not involve the use of computer systems" (p. 23).
The foundational metatheoretic aspect is ontology, which is concerned with phenomena, and hence with the properties of things and events. The assumption adopted in the model is a conventional compromise between materialist and idealist notions, referred to as dualism: There are both material realities (the Real World) and internal mind-stuff (the intellectual or Abstract World). Phenomena and their properties (such as electromagnetic radiation, the hardness and the brittleness of things, and event-duration) inhabit the Real World; whereas ideas (such as numbers, the wavelengths of colours, measures of hardness, brittleness and time, and lists of the intended functions of artefacts) are of the Abstract World.
The second aspect, epistemology, is the study of knowledge, and its sources, varieties and limits. Competing views are empiricism, which holds that knowledge is derived from sensory experience, and apriorism or rationalism, which considers that knowledge is or at least can be innate and/or derived from the human faculty of reason.
A pragmatic metatheoretic approach must support IS practitioners not only in contexts that are simple, stable and uncontroversial, but also where there is no expressible, singular, uncontested 'truth'. Some relatively closed systems, such as fly-by-wire, industrial control, and robotic assembly line management, can reasonably be treated as technical systems. In the large majority of IS, on the other hand, interaction among IT artefacts and people is intrinsic, and meaningful study of them requires the adoption of both a socio-technical perspective (Abbas & Michael 2022), and interpretivist or critical theory approaches to research. The epistemological commitment underlying the model is accordingly that knowledge depends on appropriately blending sensory experience, human imagination, and reasoning, and accommodating both tacit and codified knowledge.
The third important branch of philosophy for the present purpose, axiology, is concerned with how value is imputed to things. Organised activities depend on people, artefacts, and effective interactions among them. IS also affect people, including those participating in the system (conventionally called 'users') and some who are not participants in the system, but are affected by it (usefully referred to as 'usees' - Berleur & Drumm 1991 p.388, Clarke 1992, Fischer-Huebner & Lindskog 2001, Baumer 2015). Examples of usees include people to whom records in shared industry databases refer, such as those for police suspects, borrowers, tenants and insurees; and the conversation-partners of people whose voice and/or electronic communications are subjected to surveillance. Because of the presence and significance of users and usees in IS, human values are prominent.
Most IS involve various stakeholders with at least some differences among their value-sets. In simple contexts, the value-conflicts that arise may all be of an economic nature, particularly between the system-sponsor's operational and financial objectives and the financial interests of users. However, a range of factors can give rise to much greater complexity in the assessment of utility. The approach adopted in the pragmatic metatheoretic model is that value is dependent on the observer, that there are generally multiple observers of any given phenomenon, and hence that IS must support the integration of multiple perspectives rather than assume that one necessarily dominates (Clarke & Davison 2020), and must continue to function where tension continues among two or more perspectives.
In Clarke (2022), the model is applied and further developed in the context of identity management. A diagrammatic form of the model is in Figure 1. In the remainder of this paper, capitalised terms are defined in the text, with the full set of definitions gathered into a Glossary.
The Properties of phenomena in the Real World can be sensed by humans and artefacts with varying reliability. Within the Abstract World, two levels are then distinguished. At the Conceptual-Model level, the Real-World phenomena are conceptualised by people, in many cases on behalf of organisations. At the Data-Model level, the concepts are operationalised, enabling the Data-Items to represent the states of Properties of phenomena, in a manner that enables coherent collection, processing, management and use of the Data. These aspects of the model are not unusual. I make the claim, however, that they together provide a useful formalisation of the way in which IS practitioners view the relevant parts of the surrounding world and the representations of that world expressed in their systems.
At the Conceptual-Model level, Real-World Things and Events are represented as (Id)Entities and Transactions, and their Properties as Attibutes. Relationships exist among the various elements. The notion of a cargo-container is, in philosophical terms a 'universal' and in practical terms a category or Entity, whereas a specific cargo-container is a 'particular' or Entity-Instance. The ideas and terms used in this level are closely-related to, but not necessarily identical with, related ideas and terms in the well-developed and diverse sub-discipline of conceptual modelling.
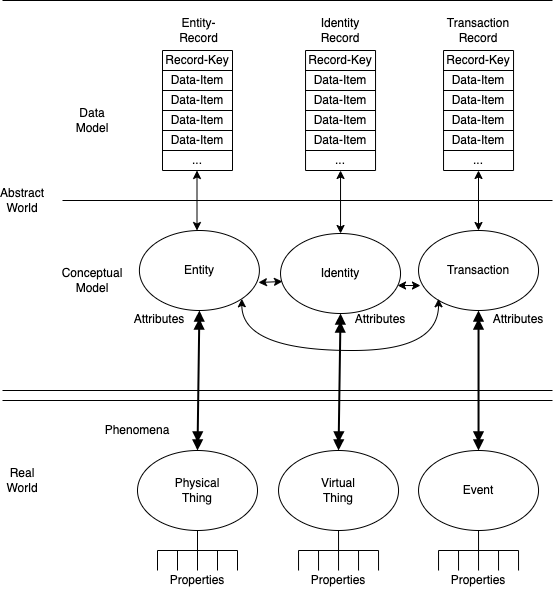
The compound and attention-attracting term (Id)Entity is used to elements of the Conceptual Model that represent Real-World Things. More specifically, an Entity corresponds with a Real-World Physical Thing, and an Identity with a Real-World Virtual Thing. Virtual Things lack the corporeal nature of a Physical Thing, but are treated as being real because they perform functions relevant to IS. Virtual Things include processes running inside computing devices, and presentations or roles, in the sense of patterns of behaviour adopted by Entities. For example, the role of CEO is an Identity that is usually performed by a single human Entity at any give time; but it is performed by different human Entities over time. The role of Company Director, on the other hand, is an Identity performed by multiple human Entities at the same time, each of whom is conceptualised as an Identity-Instance.
Virtual Things may have associations with Physical Things, e.g. a computer process with a computing device, a software-agent with a human principal, and a role with one or more humans. Some Physical Things have associations with multiple Virtual Things (e.g. devices run many processes, companies have several directors, and each individual person plays many roles). Some Virtual Things have associations with multiple Physical Things (e.g. the role of company director is performed by several individuals, as is duty fire warden). In addition, most associations are time-bounded, and some Virtual Things are associated with multiple Physical Things in succession (e.g. the series of Treasurers of an association).
Each element at the Conceptual Level has 'Attributes', which contain an 'Attribute-Value' for each instance. For example, the Entity shipping-containers has Attributes such as colour, owner, type (with Attribute-Values such as refrigerated and half-height), and various kinds of status (e.g. dirty or clean; and empty or loaded). A Relationship has the Attribute of cardinality, reflecting how many of each of the elements that it links can exist. The Attribute-Values that can be adopted is typically zero, one or many. Transactions give rise to changes in the Attribute-Values of (Id)Entities.
At the operational, Data-Model level, a Data-Item is a storage-location in which a discrete 'Data-Item-Value' can be represented. The term 'value', in this context, is generalised rather than used only in the limited, dictionary sense of "a numerical measure of a physical quantity" (OED I 4). For example, Entity-Attributes of cargo-containers may be expressed at the Data Model level as Data-Items and Data-Item-Values of Colour = Orange, Owner = MSK (indicating Danish shipping-line Maersk), Type = Half-Height, Freight-Status = Empty. The set of values permissible in a particular Data-Item can be referred to as the Domain on which it is defined.
A set of Data-Items that relate to the same (Id)Entity or Transaction make up a Record. Record-Keys are Data-Items or Data-Item groups that are capable of distinguishing which (Id)Entity-Instance a particular Record relates to. Record-Keys for Identities are called Identifiers, and Record-Keys for Entities are Entifiers. The last of those terms is unusual, perhaps original, and is further discussed below.
The final aspects of the application of the pragmatic metatheoretic model to identity management are the processes of (Id)Entification. Identification refers to the process whereby a Data-Record is associated with a particular Virtual Thing. It involves the acquisition of a Record-Key, that is to say an Identifier. The corresponding process is Entification, whereby a Data-Record is associated with a particular Physical Thing, involving the acquisition of an Entifier. Some computing devices, being a Physical Thing, have a unique number stored internally which can be reliably used as an Entifier; whereas each of the processes running within a device and communicating with remote devices is a Virtual Thing, for which a workable Identifer is the combination of IP-Address and Port-Number. For human beings, a customer-code is an Identifier, and a biometric is an Entifier.
The distinctions between Identities and Entities, and between Identifiers and Entifiers, were first proposed in Clarke (2001b), first presented in the USA in Clarke (2002a) and Clarke (2002b), and first presented in Europe and formally published in Clarke (2003b). They form parts of early versions of a comprehensive model in (Clarke 2004) and Clarke (2009). The use of Entifier in the manner defined here is evident in about 25 articles by the author within the Google Scholar catchment, which together have over 400 citations. However, there are to date very few uses of the term by other IS researchers, and no evidence has been found of the same concept referred to by an alternative term. Further, the distinction is seldom apparent in conventional identity management solutions. This aspect of the pragmatic metatheoretic model represents a major contribution to practice and theory.
The basic features of the model can deal with passive Things, including natural objects (such as gems and dinosaur bones), animals, and artefacts (such as objets d'art, pallets, and stock-items). Further articulation is needed when dealing with active Things, including artefacts capable of action in the Real World (such as computing devices and robots), and human beings. In IS that extend beyond data-processing, information production, and inferencing, to decision and even action, values loom large, conflicts among value-sets occur, and designers must take much greater care. An example of an additional complexity that arises is uncertainty about the Relationship between an Identity and an underlying Entity. If it is not known, the term Identifier is usefully replaced by the term Nym, or more specifically Anonym (if the Relationship is not knowable), or Pseudonym (if the Relationship is knowable, but not currently known).
The above presentation of the two-level model has its focus on distinguishing the concepts needed to capture sufficient of the richness of the Real World. In doing so, it has left aside questions of how reliable the assumptions are that are implicit in Data-Item-Values stored in Records that purport to relate to particular Properties of particular Real-World Things. The following section discusses the notions of an assertion and its authentication, and lays the groundwork for the subsequent discussion of the process of authenticating a number of different categories of assertion.
The pragmatic metatheoretic model outlined in the previous section postulates a Real World comprising Things and Events, which have Properties. These can be sensed by humans and artefacts with varying reliability. Authentication is a process whereby that reliability can be assessed. This paper's purpose is to present an analysis of Authentication in contexts in which Identity or Entity plays a central role. No sufficiently general body of theory has been located in the IS or any other literature. As a basis for the analysis, this sub-section accordingly summarises prior work by the author on the generic notion of Authentication (Clarke 2023).
The term Assertion is used here in the manner of OED 5: "a positive statement; a declaration, affirmation, averment", and/or OED 4: the action of making such as statement. In the present context:
An Assertion is an expression of knowledge about one of more elements of the pragmatic metatheoretic model.
The provenance of an Assertion can be of significance. The Assertion may be:
The party making the assertion may be:
Assertions are made within several different contexts, as follows:
It is common in the IT industry for the process of establishing the reliability of an Assertion to be referred to as 'Verification', or sometimes 'Validation'. Those words imply that the process delivers truth ('verity') in a Real-World context, or 'validity' in an Abstract World. In the large majority of circumstances, however, the result is not in any sense a truth, but rather a degree of assurance. It is therefore preferable to avoid those terms in favour of one that is consistent with the pragmatic model's recognition of the impracticality of the notion of humanly-accessible truth, and that interprets reliability in constructively loose terms:
Authentication is a process that establishes an appropriate degree of confidence in the reliability of an assertion.
Many factors underlie the need to avoid truth-related terminology. The Real World is complex, and it is not directly accessible by observers. Human experience of Phenomena is filtered by human perceptive and cognitive apparatus. Technological aids are designed with particular purposes in mind; they sense and measure only some aspects of particular Phenomena; and their use assumes away a range of contingencies. Added to that, high-reliability Authentication processes are generally costly to all parties concerned, in terms of monetary value, time and convenience, and intrusiveness. Processes become even more complex and less reliable where they need to cope with non-compliance by some parties, and particularly where some of the parties perceive disincentives to comply with the preferences of an organisation, or an active incentive to undermine authentication processes by adopting countermeasures. Organisations generally select a trade-off among cost, reliability, and convenience for and acceptability to the affected individuals. This inevitably results in shortfalls in the quality of the Authentication process and its conclusions. The term 'appropriate' has been included in the working definition above, to reflect the fact that the degree of confidence is compromised by, or balanced against, other factors.
Assertions in category (1) of s.2.2.1 above, relate solely to the Real World. They may be authenticated by empirical means, that is to say by observation of the Phenomena. However, observation of past Events is infeasible, and previous states of Things may also be inaccessible unless they are very stable. So it is often the case that a proxy form of Authentication has to be used, based on Data that has been previously created, perhaps processed, stored, and accessed.
Assertions in category (2) relate solely to the Abstract World. They may also be authenticated by empirical means, if the Phenomena are still accessible, enabling new Data to be gathered. Alternatively, they may be authenticated against Data available somewhere in the Abstract World. Authentication processes for such Assertions may involve the application of reasoning, in order to infer additional Assertions. There are limitations, however, depending on the particular form of reasoning used. Classical logic, most relevantly in the form of the propositional calculus, is of little practical value, because it only supports conclusions of right or wrong / true or false. Many-valued and fuzzy logics, on the other hand, recognise that propositions can have degrees of truth (Gottwald 2001). For example, three-valued logics permit an intermediate value, such as 'undefined' or 'not proven', and other forms of logic may recognise 'no information' or 'conflicting information'.
Some logics support qualitative data that makes nominal and imprecise distinctions between categories. Some other logics are appropriate to data on an ordinal scale (e.g. unborn, young, old, dead), and yet others require discrete quantitative values on an ordinal scale (such as the non-linear Richter scale for intensity of earthquakes), or even on an interval scale (with equal distances between consecutive values, cf. Celsius for temperature). A ratio scale has the further requirements of a natural zero (cf. Kelvin for temperature, Stevens 1946). Powerful inferencing tools are applicable to data on ratio scales. In order to justify applying those tools, assumptions-of-convenience are sometimes made about the data, e.g. that ordinal Likert data is on an interval scale, or that a zero can be contrived at one end of a spectrum of interval or even ordinal data.
Nomatter what approach is adopted, however, Authentication of Abstract-World Assertions cannot, alone, satisfy the criterion of 'establishing an appropriate degree of confidence', because it does nothing to test the relationship between Data and the Real World. The primary focus of Authentication processes needs to be Assertions that straddle the two Worlds. These inherently involve a check of the degree of correspondence between empirical observations of Real-World Phenomena and Data-Items in the Abstract World. To invoke an example introduced above, the category (2) Assertion 'This loan applicant has a high level of debt, so a further loan to them is risky' needs to be tested not only logically, but also against the relevant Phenomena. Without that, it may be overlooked that, for example, the loan applicant has ample net worth or an assured high income, or some of the currently outstanding loans are enjoying an interest and repayment holiday for the duration of the possible new loan, or the borrower is able to arrange a guarantor.
The term Evidence is used here in a manner related to OED III, 6: "Grounds for belief; facts or observations adduced in support of a conclusion or statement; the available body of information indicating whether an opinion or proposition is true or valid":
Evidence is Data that assists in determining the level of confidence in the reliability of an Assertion.
An individual item of Evidence is usefully referred to as an Authenticator. A common form of Authenticator is a Document, by which is meant content of any form and expressed in any medium, often text but possibly tables, diagrams, images, video or sound. Content on paper, or its electronic equivalent, continues to be a primary form. Some Authenticators carry the imprimatur of an authority, such as a registrar or notary. These are usefully referred to as a Credential (cf. OED B2: "any document used as a proof of identity or qualifications"). The term Token refers to a recording medium on which useful Data is stored.
The preliminary sections of this paper have drawn on prior work to define a pragmatic metatheoretic model to support IS practice and practice-relevant research, and to establish basic theory in relation to Assertions and their Authentication. The following section applies those ideas to the specific context of assertions in which Entities and Identities figure prominently.
This section applies the theory of authentication outlined above to Assertions that involve Entities or Identities. The first sub-section identifies the kinds of Assertion that are relevant. The later sub-sections discuss the process whereby such Assertions can be authenticated, and the nature of the Evidence that can be used in that process.
In this section, the Conceptual-Model level of the Abstract World is overlooked in favour of expressions using Data-Model terminology. In all cases, alternative expressions are readily formulated. For example, a full statement of the form " { This Identity-Instance at the Conceptual Level of an Abstract World and/or } this Identity-Record at the Data Level ... " is abbreviated to "This Identity-Record ...". Similarly, the particular World and Level-within-World are omitted, in order to reduce the length and complexity of expression, "A particular {Physical, Virtual} Thing in the Real World ..." is abbreviated to "A particular Thing ..." and "An Entity-Record or Identity-Record in the Data Model of the Abstract World ..." is abbreviated to "An (Id)Entity-Record ...".
The pragmatic metatheoretic model avoids the idea that an accessible truth exists, and articulates the relativistic notion of a degree of confidence in the reliability of statements. Reflecting this, a key term in the category descriptions below is defined as follows:
Appropriately means with a level of confidence commensurate with the reliance placed on the Assertion and the severity of the consequences if the reliance is misplaced
This sub-section identifies a set of Assertion categories. Almost all of the IS and related literature on Authentication is concerned with a limited mainstream mode of thought in which the focus is on what are referred to below as (Id)Entity Assertions - categories (1) and (2) below. Many of these sources, however, fail to distinguish Entities from Identities. For example, more than half of the 38 articles examined in AISeL evidenced these inadequacies. The small proportion of noteworthy sources found in the Bled corpus, AISeL generally, the Basket of 8 journals, and elsewhere are cited in the appropriate places in this paper.
For example, Masiero & Arvidsson (2021), citing Nyst et al. (2016, pp. 8-9), declare that "authentication indicates 'the assertion of an identity previously established during identification'" (p.907), and assume that "authenticity is proved by the Aadhaar record" (p.915, emphasis added). The Indian Aadhar record is based on biometrics, and strikes through the welfare-recipients' Identities to the underlying Entity; and the system assumes both universality and infallibility, and the authors accept those assumptions.
An assertion of a relationship between a Virtual Thing and a Record takes one of the following forms:
Expression of this Assertion category is facilitated by the industry standard Security Assertion Markup Language (SAML), which includes an assertion-type called an 'authentication statement', which asserts that 'a particular remote Virtual Thing is appropriately associated with a particular Identity' (OASIS 2005). For example, Wright & Marett (2010) refer to "design, layout, and style characteristics between authentic and fraudulent Web sites" (p.274), and discuss the means of Authentication of an Identity Assertion about a web-site.
An Assertion of a relationship between a Physical Thing and a Record takes one of the following forms:
A variant on Entity Assertion is evident. The term 'product authenticity' is used in discussions about counterfeit prescription drugs (Mavlanova & Benbunan-Fich 2009, Boos & Grote 2012, Mattke et al. 2019). Similarly, code-signing is used to detect manipulated copies of software (Clutterbuck & Rowlands 2011). A statement of the following kind might be termed a Non-Entity Assertion or an Entity Neg-Assertion:
Reflecting the axiological aspect of the pragmatic metatheoretic model, different stakeholders have different value-sets. An aspect of much of the IS literature is that it is one-sided, and favours the interests of just one of the stakeholders, most commonly the system sponsor. Counterfeit prescription drugs threaten the revenue of pharmaceutical companies, but also the health of consumers. Similarly, the authentication of artefacts (such as books, pictures and documents, but also software), may serve producers, whose concern is with revenue protection and/or the interests of consumers, who are concerned about content integrity (Kallinikos et al. 2013).
A contention of this paper is that a serious deficiency exists in the existing literature in the form of the conflation of Entity and Identity Assertions and their Authentication. A common form this takes is the common statement within the identity management industry, frequently adopted in the research literature, that Authentication is based on 'what you know, what you have, and what you are'. See, for example, Elgarah & Falaleeva (2005), Witman (2006), Carpenter et al. (2008) and Hewitt (2009). A recent UNHCR plan reported on by Madon & Schoemaker (2021) calls for "a self-managed digital wallet [that] would allow refugees to store a variety of different forms of identification such as biometric registration, individual ID documentation, attestation card and already-existing authenticated paper documents that have been digitised and uploaded" (p.938). Authenticators for Identity Assertions (such as 'I have this Accredited Refugee Code') are combined into a single Token along with an Authenticator for an Entity Assertion ('I am s/he'). Similarly, Masiero & Arvidsson (2021) declare that "authentication indicates the assertion of an identity previously established during identification" (p.907), and assume that "authenticity is proved by the Aadhaar record" (p.915). However, Aadhar is a biometric-based scheme, and hence involves an Entity not Identity Assertion.
Biometric technologies strike through a person's multiple Identities. Physical and Virtual Things differ enormously, as do the contexts, the impacts on values, and hence the design processes and the ethicality and public acceptability of those designs. It is therefore very important to distinguish between the two Assertion categories. Indicative of the seriousness of this blind spot in the IS discipline is an article in Basket of 8 journal Information Systems Research. Breward et al. (2019) conduct an acceptance study of biometric 'identification' that fails to distinguish the notions of Entifier and Identifier. The authors did not detect from either the literature or their online survey respondents that one of the important reasons for a high level of individual concern about biometrics is that they strike through to the physical person and consolidate or compromise all of that individual's identities (pp.763-764). The use of a higher-quality data collection mechanism such as interviews or focus groups would have been likely to surface deeply felt concerns, whereas surveys, even of an open-ended nature, are far less likely to expose them.
The next three Assertion categories are concerned with Properties. The descriptions here use the abbreviated form (Id)Entity to encompass both sub-categories. A straightforward Assertion takes the following form:
This category of assertion is at an atomic level and of high granularity, and relates to a Property that is represented by a single Data-Item. More complex circumstances are the subject of the following category.
To facilitate expression of Property Assertions, the industry standard SAML includes an assertion-type called an 'attribute statement', which asserts that a particular remote Virtual Thing has a particular Property (OASIS 2005).
The UNHCR plan discussed by Madon & Schoemaker (2021) includes in the envisaged "self-managed digital wallet [for] refugees" the inclusion of "education credentials" (p.938). The Token would therefore assist with the Authentication of Property Assertions (e.g. 'I have a High School Certificate from ...').
A more complex assertion depends on an inference drawn from multiple Data-Items, and takes the following form:
Reliance on Property Assertions needs to be based on careful analysis, because of their dependence on data quality, and because of the wide array of quality factors that need to be satisfied to ensure that the level of confidence in the Assertion is appropriate, defined above as meaning 'commensurate with the reliance placed on the assertion and the severity of the consequences if the reliance is misplaced'.
Kambil & van Heck (1998) describe Authentication as one of the five 'Basic Trade Processes' in Online Auctions, and used "to verify [1] the quality and [2] features of the product offered [both of which are Complex Property Assertions], [3] the authenticity of the trading parties [a combination of Identity and Attribute Assertions] ..." (p.5). This was revisited in Fairchild et al. (2007), who argued that Authentication is "central to the design of multi-attribute markets [with the market operator performing] extensive pre-qualification of suppliers by intermediary to ensure the integrity of the auction process" (pp.291-292, involving both Identity Assertions and Complex Attribute Assertions).
However, where this category is evident in the IS literature, there is often a lack of clarity as to what the Assertion is, or Assertions are, whose reliability is being investigated. An example of simple mis-phrasing is "He pays for this transaction online using BankID to authenticate his payment" (Eaton et al. 2014), when what is meant is 'He authenticates himself to his bank as a person authorised to operate on that account', i.e. it is an Identity not a Value Assertion. Wang et al. (2016) seek to distinguish between "phishing emails and authentic business emails", but without making clear whether the concern is authenticity of the content and/ or of the sender. It is feasible to design procedures to address both Assertions, but effective design is hindered if the two Assertions are not disentangled. Also evident is conflation of source (an Identity Assertion) and content (a Fact Assertion), as in the expression 'authenticity of Internet-sourced information' (e.g. Haider 2008).
A Property Assertion is frequently assumed to be dependent on an accompanying (Id)Entity Assertion; but, subject to some conditions, it is feasible, and may be far preferable (e.g. for cost, confidentiality or privacy reasons), to perform Property Assertion Authentication without (Id)Entity.
A special case of a complex Property Assertion is of considerable commercial significance, and hence is dealt with here as a separate category. An Assertion relating one Thing's ability to act on behalf of another Thing takes the following form:
This Assertion-category involves a chain of Virtual and Physical Things, and hence requires multiple Authentication processes to be performed: "The claims of a business intermediary to be acting on behalf of another intermediary need to be subjected to testing. Moreover, the claims of a person to be acting on behalf of a business entity (which may itself be acting as an intermediary for another business entity) also need to be tested. Authentication needs to be undertaken of a particular attribute or credential that reflects the agency relationship, such as a power of attorney, or some other form of delegation of power to sign contracts" (Clarke 1999, p.9). A comprehensive study of Principal-Agent Authentication is in Basu1 & Muylle (2001).
The final three Assertion Categories are entirely within the Abstract World. Authentication of these categories is not merely valuable, but actually essential to the conduct of IS. They differ from the earlier categories, however, in that Authentication of these Assertions alone, while contributing to the level of confidence, do not satisfy all of the necessary conditions, and hence complementary Assertion Authentication processes are needed, to reliably link these Assertions within the Abstract World with Things in the Real World.
Firstly, an Assertion relating to two Identities takes the following form:
Secondly, an Assertion relating to two Entities takes the following form:
The contexts in which Entity matching of humans is undertaken often have potentially very serious consequences for the person concerned. This calls for a very high degree of confidence in the reliability of the Assertion.
The third Abstract-World-only Assertion category takes the following form:
As with the previous Assertion-category, where the Physical Thing is a person, high standards are needed, in order to reflect the seriousness of the potential consequences.
Assertions are depended upon as a basis for inferencing, decision and action. They need to be authenticated, to protect against risks of error and fraud. Sources of poor quality include accidental mistakes, and intentional mistakes, including intentional false positives, e.g. masquerade or 'spoofing' to enable a person or process to exercise a power that should only be exercised by some other (Id)Entity; and intentional false negatives, e.g. avoidance, undermining or subversion of (Id)Entification. This sub-section outlines the process whereby adequate levels of reliability of Assertions can be assured. The subsequent sub-section considers the Evidence needed to support the process.
Few sources have been located that identify criteria for evaluating the quality of Authentication processes. Zviran & Erlich (2006) identify as relevant factors effectiveness, ease of implementation, ease of use, and user attitude and acceptance. Way & Yuan (2009) provide a more substantial list, comprising Accuracy, Robustness, User Acceptance, Accessibility, Feasibility, Applicability, Responsiveness, Non-reputability [sic: Non-Refutability] and Maintainability. Those authors also note different priorities for the criteria among stakeholders, which they categorise as Management, IT Support and Users. Both are useful contributions, but are mostly technical in their orientation. Given that most IS require a socio-technical approach, additional considerations need to be factored in, such as transparency (from user and usee perspectives) and costs and risks (from the viewpoint not only of the system sponsor, but also of users and usees).
Quality is a substantially greater challenge where other parties are motivated to achieve false positives or false negatives. Safeguards are needed to limit the extent to which such parties may succeed in having Assertions wrongly authenticated or wrongly rejected, in order to gain advantages for themselves or others. Techniques such as channel encryption (in particular SSL/TLS) and one-time password schemes are applied to these purposes. Each safeguard has vulnerabilities, and is subject to threats.
The level of assurance of an Authentication mechanism depends on the degree of protection against abuse, and the attractiveness to other parties of breaching the protections. It is common to distinguish multiple quality-levels of Authentication, such as unauthenticated, weakly authenticated, moderately authenticated and strongly authenticated. Strong authentication is associated with the concept of 'absolute trust', which has currency in some military and national security applications. Business enterprises and most government agencies generally adopt risk managed approaches, which accept lower levels of assurance in return for processes that are less expensive, more practical, easier to implement and use, and less intrusive.
Where the subject of the Assertion is a passive natural object, artefact or animal, the Authentication process is limited to checking the elements of the Assertion against Evidence that is already held, or is acquired from, or accessed at, an external source that is considered to be both reliable and independent of any party that stands to gain from masquerade or misinformation.
On the other hand, humans, organisations (through their human agents) and active artefacts can participate in the Authentication process, in particular in a 'challenge-response' sequence. This involves a request or 'challenge' to the relevant party for an Authenticator, and an answer or action in response, which can provide information or insight into the reliability of the Assertion. For example, at the nightclub door, a challenge is issued to show evidence of age, and a typical response is the waving of a driver's licence (a Credential) that appears to have been issued to the person who is holding it.
In section 2.4, the concepts of Authenticators, Credentials and Tokens were introduced. These notions are much applied in the Authentication of Assertions involving (Id)Entity. The central form of such Assertions is category (1), an Identity Assertion, of the form:
Each such association is achieved by means of an Identifier. The conventional term used in government circles for Authenticators designed to support Authentication of such Assertions is 'Proof of Identity' (PoI). This is a disingenuous term, implying as it does the infallibility of the Authenticator and the Authentication process that uses it. The fraud is all the more inexcusable because not only does the notion of accessible truth in such complex circumstances lack credibility, but the Evidence and the evaluation process add yet more dimensions of error and misunderstanding. An appropriate term is accordingly Evidence of Identity (EoI).
Several different categories of Authenticator are used as EoI. The notions of 'what you know' (i.e. Data of some kind) and 'what you have' (a Credential or a Token containing one) are useful summaries. It applies to humans and active artefacts, although in the case of artefacts the expression 'what you know' is better interpreted as 'what the Thing has in storage'. In each case, however, a reasonable degree of confidence in an Assertion of Identity can only be achieved if:
Common examples of knowledge-based EoI are passwords and PINs. Further instantiations are private keys generated by (or sometimes issued to) individuals' own devices (workstations, mobile phones, tablets, smartcards, etc.), and one-time passwords, whether generated by a separate device issued to the relevant individual, or communicated to them at the appropriate time over a separate and secure transmission channel. Another approach is for the Virtual Thing to present a Credential, and for the party performing the Authentication to provide a copy, of it, or Data contained in it, to an authority for such Credentials, and received a confirmation that the copy or Data corresponds with the Data held by that authority.
Tokens are usefully applied to the storage of human-visible and/or machine-readable copies of (Id)Entifiers. The same Token may also be used as EoI, by containing one or more Authenticators, which may be Credentials issued by an authority. A simple form of such possession-based EoI is a 'turnaround document' which is provided to the relevant person or artefact, carried, and presented when needed. Various kinds of 'identity card' exist. A familiar form is credit-card-sized plastic card carrying a chip, sometimes called a smartcard. Another, specific-purpose design is a sequentially-numbered ticket issued to each person required to wait in a queue. Other designs use machine-readable visual images (such as bar-codes and QR-codes) and machine-readable data-storage (such as a magnetic-stripe, solid-state memory in such artefacts as a thumbdrive or 'USB key', and transmission from an RFID-tag).
In some circumstances, the provision of an Identifier may represent EoI. For example, if a Token is used, and not even the artefact or the individual is aware of the Data-Value that is their Identifier, but the authenticating party (or its technological artefact) knows that Data-Value, the Identifier itself can represent reliable EoI. Generally, however, an Identifier is not a secret, and most schemes use Data-Item(s) other than Identifiers.
The next Assertion category (2), an Entity Assertion, is of the form:
The Record-Key, in this case an Entifier, by definition reliably distinguishes that Entity-Instance from all other Instances of the same Entity. An Authenticator for this purpose, EoE, differs from EoI, in that it is required to provide strong support for the proposition that the Physical Thing is a specific object, artefact or human.
An example is a Token installed in a device that provides the relevant Data to, and only to, the party doing the Authentication. Subject to careful design of the EoE creation, installation and storage, and of the communications protocols including transmission security features, a considerable degree of confidence can be designed into such a scheme. In the case of animals and humans, a biometric measure may be used. Alternatively, an animal, or a human, can be subjected to implantation of a Token in the same manner as installation in an artefact (Michael & Michael 2009).
Assertion categories (3) to (5) all involve Property Assertions. Simplifying:
Two alternative approaches to the Authentication of Property Assertions are possible. Reliance may be placed on Evidence in such forms as Assertions containing sufficient detail that can be checked against one or more other sources (e.g. a claim of a qualification against a testamur, or against a database listing graduates; or a statement that a particular level of no-claim bonus has been achieved with a particular insurer against a Document that purports to have been issued by that insurer). Greater weight is generally warranted where the Credential is issued by a party that is in some sense authoritative.
The alternative approach is for the party performing the Authentication to rely on Data that they already hold. The relevant (Id)Entity Record may contain a directly-relevant Data-Item, such as a flag for 'Trade Customer' or 'Old-Age Pensioner', or for some category of disablement such as 'legally blind'. In other cases, it will be necessary for the organisation to apply logical processes to its Data to assess the claim. This applies, for example, to a claim of being owed a refund for a failed delivery; to a claim of having qualified for a loyalty bonus or a no-claim bonus; or to having reached a particular age or period of association with an organisation.
This sub-section has assumed the existence of the relevant Authenticator. It is also necessary to discuss how Authenticators come into being. The establishment of an Authenticator is commonly performed during an Enrolment phase, when a new Thing registers with an organisation.
Enrolment generally involves the conduct of a first-round of reasonably thorough Authentication activities in relation to the relevant Assertion category/ies. This may rely, for example, on Credentials issued by an authority that has (or, in many cases, is merely assumed to have) undertaken some form of Authentication prior to issuing it, such as a birth certificate, certificate of naturalisation, marriage certificate, passport, driver's licence (and, in some jurisdictions, non-driver's 'licence'), employer-issued building security card, credit card, club membership card, statutory declaration, affidavit, and/or letter of introduction. This may attest to the (Id)entity itself (although most do so in an at least somewhat loose manner), and/or to an (Id)Entity Attribute, such as birthdate, a licence to drive an articulated vehicle, or nationality.
Commonly, an Authenticator is created by one party and agreed with or issued to another. The creator may or may not also be the party that will rely on the Authenticator. The relying party has an interest in the Authenticator being created in a manner that ensures its integrity. The party whose (Id)Entity and/or Property is being checked has an interest in gaining the Authenticator, and in either preventing error and inappropriate behaviour by the Authenticator (if they have a legitimate claim) or encouraging erroneous creation (if their claim is not legitimate or not well-documented). The party creating the Authenticator, meanwhile, has its own interests to protect (such as cost reduction, revenue production, limitation of liability and reputation), which may conflict with the integrity objective.
The final steps are the creation of an (Id)Entity Record - a sub-process sometimes referred to as Registration - and then the establishment of means whereby an effective but also efficient Authentication process can be conducted on the subsequent occasions when a party presents, commonly using a password, PIN, Token or one-time password channel,.
An assumption is commonly made in the identity management industry that the (Id)Entifier involved in Property Authentication is automatically and necessarily known to the party performing the Authentication process. The assumption is inappropriate, because in many circumstances it is feasible to achieve appropriate degrees of confidence in an Assertion without disclosure of (Id)Entity. This is the case not only for Assertion-categories 1 and 2, of (Id)Entity, but also for the several categories of Property Assertions.
Little material has been found that identifies criteria for data quality in support of Authentication processes. It is therefore necessary to got back to basic principles and work forward from there. Whether Data is a 'reliable representation' of the relevant phenomena depends on Data Quality factors (which are assessable at the time of creation and subsequently) and Information Quality factors (which are assessable only at the time of use). See Table 1. The development of this categorisation drew on, in particular, Huh et al. (1990), van der Pijl (1994), Wand & Wang (1996), Wang & Strong (1996), Shanks & Darke (1998), Shanks & Corbitt (1999) and Piprani & Ernst (2008).
Adapted from Clarke (2016), Table 1
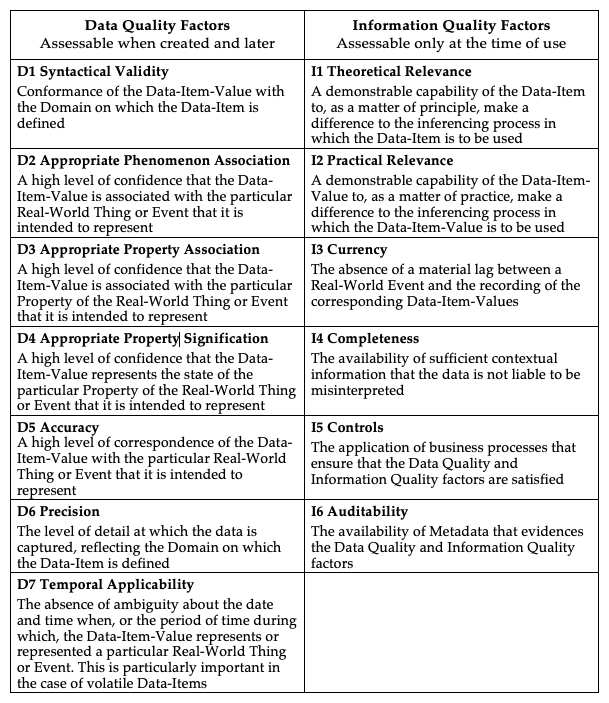
The generic categorisation of quality factors in Table 1 needs to be applied to each circumstance. For example, an Identity Authenticator for a role may be vital to the signing of a large contract, in which case D7 (Temporal Applicability) looms as a high priority for careful checking. Another concern, causing people to be justifiably wary of government agencies sharing data, is that that D3 (Appropriate Property Association) and D4 (Appropriate Property Signification) differ greatly, depending on context. The number of children a person declares to an agency depends on that agency's definition of 'a child of a person' (and definitions may even differ between programs administered by the same agency, and over time). The same holds for marital status, and for gender. More complex examples are legion, such as a person's income, which can be measured differently, and can be accumulated and/or averaged over periods as diverse as daily and annually.
Quality assurance measures needs to be layered. Safeguards must be designed into authentication processes, and implemented. Controls must be designed, implemented and monitored, to ensure that the safeguards are operational and effective. When concern arises that an Authentication process may have been malperformed or delivered a wrong result, it is necessary to conduct an audit. This depends on reviewability, replicability, auditability, accountability, and action. Where quality shortfalls occur, additional considerations come into play, including the following:
Further processes need to exist, and to be implemented when material errors are suspected. These comprise means of seeking review and appealing, investigation, evaluation, decision, accountability, sanctions and enforcement.
However, for any of these measures to be feasible, Data needs to be available that document the basis on which each decision was made. To enable that, when an Authentication process is performed, metadata needs to be recorded. That metadata may be as much as a complete, additional copy of every Data-Item-Value involved in the process, or as little as the facts that Authentication was conducted and that adequate evidence in support of the Assertion was present. How much metadata is retained needs to reflect such factors as cost and the sensitivity of each Data-Item and Data-Item-Value involved in the process.
Quality is a substantially greater challenge where other parties are motivated to contrive false positives or false negatives. Safeguards are needed to limit the extent to which such parties may succeed in having Assertions wrongly accepted or wrongly rejected, in order to gain advantages for themselves or others.
This section has articulated the basic theory of Authentication in contexts relevant to identity management activities in IS. It identifies a range of needs. Areas in which IS practice and theory evidence shortfalls include the widespread error of conflating Identity and Entity, failure to be clear about what actions need Authentication, failure to evaluate threats and the effectiveness of relevant safeguards, resulting in inability to rationally select a good-enough approach to Assertion Authentication.
The analysis presented above has important implications for IS practitioners, and for practice-oriented IS research. Some of these relate to the quality of IS design, while others reflect the importance of the human-values aspects of IS activities.
Attention has been drawn to the significant differences between Entities that reflect Physical Things and Identities that reflect Virtual Things. Associated with this is the failure to distinguish Entifiers from Identifiers, and to recognise the differences between the processes of Entification and Identification. The ability of an IS to support organisational activities is undermined if the model on which it is built conflates an Entifier such as a device-id with an Identifier of one of many processes running within that device. In such circumstances, users of a cybersecurity-monitoring system, for example, would be hampered in their efforts to detect runaway, rogue and compromised processes. Similarly, confusion could arise between a non-corporeal principal (such as a corporate trustee) and the individual person or software-process acting as the agent for that principal.
In the case of humans, the failure to distinguish Entities from Identities means there is an implicit assumption that a person whose Assertion of Identity is authenticated is necessarily a particular instance of homo sapiens. The Authenticators used by older family members continue to be provided to younger members, so that ATM and EFTPOS transactions can be conducted by means of card and PIN; Internet credit-card transactions by means of credit-card details and 'security code'; and Internet account login by password. The same pattern is repeated by very old family members entrusting their Authenticators to middle-aged family members they consider trustworthy. Commercial terms may well provide organisations with legal assurance that (if they can gather evidence) they can repudiate responsibility for transactions conducted in such ways. On the other hand, all of the organisation's work on risk assessment and risk management, including distinguishing between abuse of commercial terms by the principal and abuse by another party through unauthorised masquerade, lie outside the model, and hence unsupportable by the IS.
Another technical problem that is masked by conventional, inadequate identity management models is the risk of biometrics being compromised, such that convincing biometrics-based masquerade is able to be committed. The Properties of Physical Things that are used for biometrics (fingerprints, iris-patterns, password-capture dynamics, gait, DNA, etc.), are not capable of being tightly protected. They can be captured and replicated, then simulated sufficiently well that Entity Authentication can be duped. Each advance in liveness-testing, for example, stimulates countermeasures.
This suggests that the value of biometrics-based Entification may fall and/or that governments may move to limit its use to tightly-controlled, priority circumstances. This would be tantamount to imposing a licensing scheme and heavily-sanctioned legal prohibitions on retention and transmission of biometric data. PIN-pads were designed to prevent capture, retention, replay and transmission of PINs. The same design approach can be applied to biometrics, by implementing a secure stored-biometric measure in a personal card, and installing a secure capture and processing module in the authentication device (Clarke 2003a). This has recently become more common in the form of separation of Authentication of an individual's Entity Assertion to their personal device (e.g. mobile phone, tablet) from Authentication of the device's Entity Assertion and/or of each process's Identity Assertion to a remote service.
The widespread availability of high-capacity information infrastructure since the 1990s has had impacts on many aspects of organisational and individual activity. One key aspect is greatly increased institutional distance. For example, until the turn of the century, consumer credit business processes embodied a blend of Authentication of both category (2) and category (3) Assertions, because they were 'high-touch' in nature. Since then, most business enterprises have abandoned such labour-intensive approaches, and are now remote from their clients, with decision-making made on the basis of a Digital Persona rather than the person (Clarke 1994a, 2014). Moreover, the recent fashions of big data, data analytics and AI/ML, by increasing the volume and diversity of data being used, and decreasing the transparency of the decision process, have greatly increased the scope for erroneous inferences. Authentication of category (3) Assertions are curtailed or dropped, and the much weaker form of Authentication of category (2) Assertions relied upon instead, because they are easily automated and inexpensive and quick.
These factors have given rise to greatly increased scope for faulty business decisions. These are not limited to the example used above, consumer credit, but pervade many other application areas. Some of the harm directly affects the organisation sponsoring the system, e.g. through faulty evaluations of loan-worthiness. In many cases, however, the harm is suffered by users and usees. The infliction of harm may not come to the organisation's attention for some time, resulting in reputational risk. Imprecisions in the models underlying identity management schemes exacerbate these risks, and hence far greater care is needed in IS design than in the past. There are few signs, however, that appropriate changes are being made to safeguards, controls and mechanisms for redress.
The reduction in the effectiveness of identity management noted in the previous sub-section, can have efficiency and financial dimensions. Reduced reputation harms market-share and sales volumes, and hence increases the gross profit margin needed to cover the overheads. In industry sectors in which consumer protection and other regulatory mechanisms exist, the scope exists for customer complaints numbers to rocket, and with that complaints-handling costs. Restitution and redress to individual complainants can be greatly exceeded by even the legal costs of a class action, and swamped by a damages settlement.
The previous sub-section also noted the concerns of individuals about Entification processes, biometrics and a consolidated Digital Persona, and the risks of data-leakage and and manipulation that they give rise to. Even Identification processes are of concern, especially where organisations have the capacity to inter-link multiple of a person's many Identities. This results in tensions between the organisation and individual users, both employees of the sponsoring organisation, and individual usees. Those tensions play out in avoidance, obfuscation, falsification, and lowered ethicality of behaviour and loyalty among individuals with whom the organisation interacts, and in many cases on which it depends. Identity Authentication, and particularly Entity Authentication, are expensive, both in terms of financial costs and negative impacts on users and usees. This raises the question as to whether the Authentication of other forms of Assertion may be able to deliver sufficient assurance to an organisation, and to be performed materially less expensively.
This paper has identified three forms of Attribute Authentication, each of which can be devised in many contexts without having to perform (Id)Entification and (Id)Entity Authentiation processes. In addition, the prior paper which presents a generic theory of authentication identifies several other Assertion-categories that can be effective in satisfying organisations' needs, and can be at the same time more efficient. These are Fact Assertions, Content Integrity Assertions, Liquid-Asset Value Assertions and Non-Liquid-Asset Value Assertions (Clarke 2023).
Remarkably few sources have been located that give systematic consideration to the Authentication of Assertions other than of (Id)Entity. Exceptions include Clarke (2001), which argued that "parties [need to] know what is being authenticated" (p.148), and gave examples of Value and Attribute Assertions; Rauniar et al. (2002), which distinguished user authentication, smartcard authentication and card-reader authentication; and Clarke (2003b), which listed "Assertions important to eBusiness" as extending to organisational and artefact Entities and Identities, Attributes, Agency (referred to in this paper as a Principal-Agent Assertion), Location and Value. The absence of serious treatment in the literature is remarkable given the relative ease and inexpensiveness of Authentication of some of the other categories of Assertion, at least in a proportion of the circumstances in which activities are conducted.
The primary focus in the first three sub-sections above has been the interests of the organisational sponsor of the particular IS. This final sub-section broadens the view to include stakeholders generally.
Many circumstances arise in which Authentication of any category of Assertion, and Authentication of (Id)Entity Assertions in particular involve clashes of values between the system sponsor and individual users and usees. In some of those circumstances, the tension is intrinsic and largely unavoidable. For example, in both the lending and the insurance sectors, the contracting organisation is unlikely to be able to protect their financial interest unless key Assertions by the other party can be reliably authenticated. Similarly, government agencies that make transfer payments to the needy have an obligation to authenticate the claims made by each applicant. There are many circumstances, however, in which an appreciation of the full range of Authentication possibilities may enable the discovery of scope for the organisation to adopt less intrusive process designs. Individuals live their lives in enormously varied circumstances. Organisations that understand particular customer segments may be able to offer alternative Assertion-Authentication channels for, say, the seriously sight- or mobility-impaired, or for victims of domestic violence who are currently taking great care not to disclose their whereabouts.
More generally, many people are concerned about the conflation of their separate Identities. Some have reasons that derive from a desire for physical safety, others because of an enclosed disposition, some because of embarrassing personal histories, and of course some for reasons that may deleteriously affect the interests of an organisation they deal with. All such categories of people are likely to be concerned about the conflation of roles they perform on behalf of an employer with their roles on behalf of associations, clubs, their families, and their friends. Some people are even more concerned about the conflation of their Identities with multiple consumer marketing corporations, and even more so as public-private partnerships proliferate, government agency databases are compromised, and a movement gathers steam that began as a gleam in the eye of a Google CEO and Chair: the high-tech, corporatised-government State (Schmidt & Cohen 2013). This is inherent in Entifiers, but also increasingly common with Identifiers, where governments and consumer marketing corporations alike invest heavily in the consolidation of personal data into a singular Digital Persona. Many individuals are very concerned about the enablement of surveillance and manipulation, the creation of 'honey-pots' that attract additional parties, the inevitable abuse of insider privileges, and leakage of sensitive personal information.
Arguments can be advanced for organisations to take individuals' interests into account for ethical, consumer rights or social responsibility reasons. Leaving those aside, however, organisational self-interest may well be best served by recognising the extent to which individual user behaviour, especially among employees and contractors, and usee behaviour, may not be what the organisation prefers. Specifically, individuals' behaviour may include objections, non-adoption, non-compliance, avoidance, obfuscation, falsification, quiet sabotage, and whistleblowing. These drive up an organisation's costs, and drive down its internal morale and its external reputation. Opportunities exist to apply insights from the model and analysis presented in this paper to envision and implement satisfactory forms of Authentication that are less burdensome and intrusive for individuals and less expensive and otherwise harmful for organisations.
This paper has built on a previously-published pragmatic metatheoretic model, that is intended to reflect the Real World and the Abstract Worlds as they are understood and manipulated in IS practice and practice-oriented IS research. It has drawn further on previously-published extension of that model into the identity management space, and a generic theory of Authentication of Assertion categories relevant to IS.
The first contribution of this paper is a body of theory that identifies eight categories of Assertion that involve (Id)Entity, outlines key requirements of processes for the Authentication of those Assertion categories, describes the forms that may be taken by Evidence that can support those processes, and provides a framework for the evaluation of Data Quality and Information Quality of that Evidence.
A second area of contribution is the discussion of the implications of this body of theory for IS practice, and for the organisations that depend on the products of IS practitioners. Proposals are made for improvements in effectiveness and efficiency within the frame of reference used by the organisations that utilise IS. Further proposals are made that reflect the somewhat different worldviews of those organisations' employees, customers and suppliers, and of usees, who are affected by but do not directly participate in the system. These have the capacity to undermine and disrupt the achievement of the system sponsor's aims. Many of those worldviews also have a degree of legitimacy that deserves attention for its own sake, and that may gain support from powerful organisations elsewhere in the organisation's environment.
At a more detailed level, the analysis presented in this paper identifies a number of weak spots in IS and practice, and points towards ways to address them. The most significant weakness, visited at multiple points in the paper, is the conflation of the concepts of Identity and Entity, and how that plays out in faulty business models and ineffective, inefficient and unpopular business processes.
Beyond these implications for IS practice, new directions for practice-oriented IS research are opened up. More illustrations and applications of the model will deliver deeper insights that offer value in particular contexts. Some industry sectors deal in natural objects and passive artefacts, both physical and virtual, whose Properties may demand refinements and extensions of a model and theory that are intentionally somewhat generic.
Active artefacts, again both physical and virtual, are increasingly being conceived and injected into IS. There is current controversy concerning the extent to which they can reliably be delegated the power to infer, decide and act in isolation, or need to be oriented towards decision support roles, working closely with humans. The elements of the above analysis of (Id)Entification, and of the Authentication of (Id)Entity Assertions, provide what may prove to be valuable perspectives on the problem-domain. Another area in which considerable scope exists for insightful work is the ways in which organisations, as Virtual Things, are represented within IS models, and how the reliability of Assertions relating to them can be evaluated.
Abbas R. & Michael K. (2022) 'Socio-Technical Theory: A review' In S. Papagiannidis (Ed), 'TheoryHub Book', TheoryHub, 2022, at https://open.ncl.ac.uk/theories/9/socio-technical-theory/
Altinkemer K. & Wang T. (2011) 'Cost and benefit analysis of authentication systems' Decision Support Systems 51 (2011) 394-404
Avison D. & Fitzgerald G. (2006) 'Information Systems Development - Methodologies, Techniques & Tools' McGraw Hill, 4th ed., 2006
Basu1 A. & Muylle S. (2001) 'Achieving Authentication in Electronic Markets: A Principal-Agent Perspective' Proc. 8th Research Symposium on Emerging Electronic Markets, Maastricht, The Netherlands, September 2001, at https://citeseerx.ist.psu.edu/document?repid=rep1&type=pdf&doi=538ce0bbebb44ce015995e3e5122092a3fa93171
Baumer E.P.S. (2015) 'Usees' Proc. 33rd Annual ACM Conference on Human Factors in Computing Systems (CHI'15), April 2015, at http://ericbaumer.com/2015/01/07/usees/
Berleur J. & Drumm J. (Eds.) (1991) 'Information Technology Assessment' Proc. 4th IFIP-TC9 International Conference on Human Choice and Computers, Dublin, July 8-12, 1990, Elsevier Science Publishers (North-Holland), 1991
Boos D. & Grote G. (2012) 'Designing Controllable Accountabilities of Future Internet of Things Applications' Scandinavian Journal of Information Systems 24,1, at 1
Brands S.A. (2000) 'Rethinking Public Key Infrastructures and Digital Certificates: Building in Privacy' MIT Press, 2000
Breward M., Hassanein K. & Head M. (2017) 'Understanding Consumers' Attitudes Toward Controversial Information Technologies: A Contextualization Approach' Information Systems Research 28,4 (2017) 760-774
Carpenter D.R., McLeod A.J. & Clark J.G. (2008) 'Using Biometric Authentication to Improve Fire Ground Accountability: An Assessment of Firefighter Privacy Concerns' Proc. AMCIS 2008, at 11
Chaum D. (1985) 'Security Without Identification: Transaction Systems To Make Big Brother Obsolete' Communications of the ACM 28, 10 (October 1985) 1030-1044, at ://dl.acm.org/doi/pdf/10.1145/4372.4373
Clarke R. (1992) 'Extra-Organisational Systems: A Challenge to the Software Engineering Paradigm' Proc. IFIP World Congress, Madrid, September 1992, PrePrint at http://www.rogerclarke.com/SOS/PaperExtraOrgSys.html
Clarke R. (1994a) 'The Digital Persona and its Application to Data Surveillance' The Information Society 10,2 (June 1994) 77-92, PrePrint at http://www.rogerclarke.com/DV/DigPersona.html
Clarke R. (1994b) 'Human Identification in Information Systems: Management Challenges and Public Policy Issues' Information Technology & People 7,4 (December 1994) 6-37, PrePrint at ://www.rogerclarke.com/DV/HumanID.html
Clarke R. (1999) 'Identified, Anonymous and Pseudonymous Transactions: The Spectrum of Choice' Proc. Conf. User Identification & Privacy Protection Conference, Stockholm, June 1999, PrePrint at http://www.rogerclarke.com/DV/UIPP99.html
Clarke R. (2001a) 'The Fundamental Inadequacies of Conventional Public Key Infrastructure' Proc. Conf. ECIS'2001, Bled, Slovenia, 27-29 June 2001, PrePrint at http://www.rogerclarke.com/II/ECIS2001.html
Clarke R. (2001b) 'Authentication: A Sufficiently Rich Model to Enable e-Business' Xamax Consultancy Pty Ltd, 19 October 2001, at http://www.rogerclarke.com/EC/AuthModel.html011019.html
Clarke R. (2002a) 'Personal Notes on Computers, Freedom & Privacy 2002' CFP'22, San Francisco, Xamax Consultancy Pty Ltd, 16-19 April 2002, at http://rogerclarke.com/DV/NotesCFP02.html
Clarke R. (2002b) 'Why Do We Need PKI? Authentication Re-visited' Xamax Consultancy Pty Ltd, Presentation at the 1st Annual PKI Research Workshop, at NIST, Gaithersburg MD, April 24-25, 2002, at http://www.rogerclarke.com/EC/PKIRW02.html
Clarke R. (2003a) 'The Scope for Privacy-Sensitive Biometric Architecture' Xamax Consultancy Pty Ltd, February 2003, at http://www.rogerclarke.com/DV/BioArch.html
Clarke R. (2003b) 'Authentication Re-visited: How Public Key Infrastructure Could Yet Prosper' Proc. 16th Bled eCommerce Conf., June 2003, PrePrint at http://www.rogerclarke.com/EC/Bled03.html
Clarke R. (2004) 'Identity Management: The Technologies Their Business Value Their Problems Their Prospects' Xamax Consultancxy Pty Ltd, March 2004, 66 pp., at http://www.xamax.com.au/EC/IdMngt-Public.pdf
Clarke R. (2009) 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' Proc. IDIS 2009 - The 2nd Multidisciplinary Workshop on Identity in the Information Society, LSE, London, 5 June 2009, at http://www.rogerclarke.com/ID/IdModel-090605.html
Clarke R. (2014) 'Promise Unfulfilled: The Digital Persona Concept, Two Decades Later' Information Technology & People 27, 2 (Jun 2014) 182-207, PrePrint at http://www.rogerclarke.com/ID/DP12.html
Clarke R. (2016) 'Big Data, Big Risks' Information Systems Journal 26, 1 (January 2016) 77-90, PrePrint at http://www.rogerclarke.com/EC/BDBR.html
Clarke R. (2021) 'A Platform for a Pragmatic Metatheoretic Model for Information Systems Practice and Research' Proc. Austral. Conf. Infor. Syst. (ACIS), December 2021, PrePrint at http://rogerclarke.com/ID/PMM.html
Clarke R. (2022) 'A Reconsideration of the Foundations of Identity Management' Proc. 35th Bled eConference, June 2022, pp.1-30, PrePrint at http://rogerclarke.com/ID/IDM-Bled.html
Clarke R. (2023) ''A Generic Theory of Authentication to Support IS Practice and Research' Xamax Consultancy Pty Ltd, January 2023, at http://rogerclarke.com/ID/PGTA.html
Clarke R. & Davidson R.M. (2020) 'Through Whose Eyes? The Critical Concept of Researcher Perspective' J. Assoc. Infor. Syst. 21, 2 (March-April 2020) 483-501, PrePrint at http://rogerclarke.com/SOS/RP.html
Clutterbuck P. & Rowlands T. (2011) 'An Extended Public Key Infrastructure Framework For Host-Based Information Security Management' Proc. PACIS 2011, at 48
Eaton B., Hallingby H.K., Nesse P.-J. & Hanseth O. (2014) 'Achieving Payoffs from an Industry Cloud Ecosystem at BankID' MIS Quarterly Executive 13,4 at 6
Elgarah W. & Falaleeva N. (2005) 'Adoption of Biometric Technology: Information Privacy in TAM' Proc. AMCIS 2005, at 222
Fairchild A.M., O'Reilly P., Finnegan P. & Ribbers P.M. (2007) 'Multi-Criteria Markets: An Exploratory Study of Market Process Design' Electronic Markets 17,4, (Nov 2007) 286-297, at http://www.electronicmarkets.org/fileadmin/user_upload/doc/Issues/Volume_17/Issue_04/V17I4_Multi-Criteria_Markets__An_Exploratory_Study_of_Market_Process_Design.pdf
Fischer-Huebner S. & Lindskog H. (2001) 'Teaching Privacy-Enhancing Technologies' Proc. IFIP WG 11.8 2nd World Conf. on Information Security Education, Perth, Australia
Gottwald S. (2001) 'A Treatise on Many-Valued Logics', January 2001, at https://www.researchgate.net/profile/Siegfried-Gottwald/publication/259645593_A_Treatise_on_Many-Valued_Logics/links/00b7d5324ce793473c000000/A-Treatise-on-Many-Valued-Logics.pdf
Haider A. (2008) 'Believable Unbelievable Internet Based Information' Proc. ACIS 2008, at 93
Hewitt B. (2009) 'Using a Hybrid Technology Acceptance Model to Explore How Security Measures Affect the Adoption of Electronic Health Record Systems' Proc. AMCIS 2009, at 328
Huh Y.U., Keller F.R., Redman T.C. & Watkins A.R. (1990) 'Data Quality' Information and Software Technology 32, 8 (1990) 559-565
IETF (2022) 'RFCs' Internet Engineering Task Force (IETF), December 2022, at https://www.ietf.org/standards/rfcs/
Kallinikos J., Aaltonen A. & Marton A. (2013) 'The Ambivalent Ontology of Digital Artifacts' MIS Quarterly 37,2 (June 2013) 357-370
Kambil A. & van Heck E. (1998) 'Reengineering the Dutch Flower Auctions' Information Systems Research 9,1 (March 1998) 1-19
Magnusson A. (2022) 'The Definitive Guide to Authentication' Strong DM, September 2022, at https://www.strongdm.com/authentication
Masiero S. & Arvidsson V. (2021) 'Degenerative outcomes of digital identity platforms for development' Information Systems Journal 31,6 (2021) 903-928, at https://doi-org.virtual.anu.edu.au/10.1111/isj.12351
Mattke J., Maier C., Hund A. & Weitzel T. (2019) 'How an Enterprise Blockchain Application in the U.S. Pharmaceuticals Supply Chain is Saving Lives' MIS Quarterly Executive 18,4 at 6
Mavlanova T. & Benbunan-Fich R. (2009) 'The Effect of Product Presentation and Website Trust Features on the Perception of Counterfeit Deception' Proc. AMCIS 2009, 698
Michael K. & Michael M.G. (2009) 'Innovative Automatic Identification and Location-based Services: From Bar Codes to Chip Implants' Information Science Reference, 2009
Mumford E. (2006) 'The story of socio-technical design: reflections on its successes, failures and potential' Info Systems J 16 (2006) 317-342, at https://executiveinsight.typepad.com/files/the-story-of-socio-technical-design.pdf
Nyst C., Makin P., Pannifer S. & Whitley E. (2016) 'Digital identity: Issue analysis: Executive summary' Consult Hyperion, 2016
OASIS (2005) 'SAML V2.0 Standard' OASIS, March 2005, at https://wiki.oasis-open.org/security/FrontPage
van der Pijl G. (1994) 'Measuring the strategic dimensions of the quality of information' Journal of Strategic Information Systems 3, 3 (1994) 179-190
Piprani B. & Ernst D. (2008) 'A Model for Data Quality Assessment' Proc. OTM Workshops (5333) 2008, pp 750-759
Rauniar R, Rauniar D., Shakya S. & Urcuyo C. (2002) 'A Mutual Authentication Scheme for Low Cost Smart Card Applications' Proc. AMCIS 2002, at 265
Ryan T.W. & Marett K. (2010) 'The Influence of Experiential and Dispositional Factors in Phishing: An Empirical Investigation of the Deceived' Journal of Management Information Systems 27,1 (Summer 2010) 273-303
Schmidt E. & Cohen J. (2013) 'The New Digital Age: Reshaping the Future of People, Nations and Business' Knopf, 2013
Shanks G. & Corbitt B. (1999) 'Understanding Data Quality: Social and Cultural Aspects' Proc. 10th Australasian Conf. on Info. Syst., 1999
Stevens S.S. (1946) 'On the Theory of Scales of Measurement' Science 103, 2684 (7 June 1946), at https://psychology.okstate.edu/faculty/jgrice/psyc3120/Stevens_FourScales_1946.pdf
Wand Y. & Wang R.Y. (1996) 'Anchoring Data Quality Dimensions in Ontological Foundations' Commun. ACM 39, 11 (November 1996) 86-95
Wang J., Li Y. & and Rao H.R. (2016) 'Overconfidence in Phishing Email Detection' Journal of the Association for Information Systems 17,11 (2016) 759-783
Wang R.Y. & Strong D.M. (1996) 'Beyond Accuracy: What Data Quality Means to Data Consumers' Journal of Management Information Systems 12, 4 (Spring, 1996) 5-33
Way S.C. & Yuan Y. (2009) 'Criteria for Evaluating Authentication Systems' Proc. AMCIS 2009, at 338
Witman P. (2006) 'Anti-Phishing Strong Authentication Technology Options' Proc. AMCIS 2006, at 131
Zviran M. & Erlich Z. (2006) 'Identification and Authentication: Technology and Implementation Issues' Commun. Assoc. Infor. Syst. 17,4 (2006) 90-105
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor associated with the Allens Hub for Technology, Law and Innovation in UNSW Law, and a Visiting Professor in the Research School of Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: DATE - Last Amended: 13 March 2023 by 3 April 2021 - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/ID/IEA.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy