Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Preliminary Draft of 19 October 2001. The substantive version is at http://www.rogerclarke.com/EC/AuthModel.html
© Xamax Consultancy Pty Ltd, 2001
This document is at http://www.rogerclarke.com/EC/AuthModel.html011019.html
It has been conventional for some years to presume that e-commerce is dependent upon the parties to transactions being identified, and their identities authenticated. This paper examines the concepts of identification and authentication as they apply to people and organisations. It suggests that many of the conventional presumptions are misguided, and presents a model and definitions that it is argued will lay the appropriate foundation for real progress in the e-business arena.
The terms 'identification' and 'authentication' are much-used in the context of e-business. This paper proposes that they are also much-misunderstood, and that the failure to grasp their real meaning and their import is seriously detrimental to, at one and the same time, the adoption of e-commerce, the achievement of effective and efficient e-government, personal liberties, and social stability and cohesion.
A cluster of concepts is introduced using a popular aphorism. Identification is then considered, as it relates to both humans and organisations. The processes of authentication are then examined, not only of identity, but also of other kinds of assertion that are relevant to e-business. Anonymity and pseudonymity are defined, and the concept of a nym introduced. Implications of the model and definitions are outlined.
Literature and prior publications on which the analysis is based are provided in the bibliography. Where terms are used in specific ways, they are shown in the text in bold-faced type in the paragraph in which they are defined.
Before embarking on the analysis, it is useful to provide a brief overview of the subject-matter that this paper addresses. This is done by means of Steiner's archetypal cartoon in the New Yorker magazine in 1993, which so captured the mood of that moment, at the dawn of the cyberspace era:

Several elements relevant to this paper can be discerned in the cartoon. They are:
If there is a moral to be found in the cartoon, it might be that, when you're using the Internet, you have only a limited amount of information available to you, and you need to be cautious about assumptions you make. In particular situations, there are various things that you might find worth authenticating before you place reliance on information, or take actions. Examples of such situations include where you provide your credit card details, utter confidences to your conversation-partner, open a file that someone has sent you, or pass on information you've received, such as investment tips, or virus warnings.
In such circumstances, you might be well-advised to collect some information about one or more of the following:
These various kinds of checking may be entirely independent from one another. In particular, knowing who your conversation-partner is is not a pre-condition for knowing the others. For example, if your bank confirms that the requisite funds have arrived in your account, you can carry out your part of the bargain with confidence, without knowing which person (or dog) you sold your goods or services to. Similarly, an on-line grief counsellor doesn't need to know the driver's licence number or commonly-used name of a client, provided that they're confident that it's the same 'Bill' or 'Susan' that they were talking to yesterday. And 'Bill' or 'Susan', while they may seek assurance about the counsellor's qualifications and undertakings of confidentiality, are not likely to seek (and are even less likely to be provided with) the counsellor's commonly-used name, home-address and home telephone number.
The New Yorker cartoon charms us, because it encapsulates the above information (and probably much more) in a brisk and engaging way. The remainder of this paper adopts the much cooler and more analytical manner necessary to establish a foundation for systems design.
The analysis commences with the conventional ontological assumption that there is a real world of things, and an abstract world of information. The application of telecommunications-based tools to the business of corporations and government agencies, hereafter referred to as e-business, is dependent on relevant entities in the real world being modelled in databases.
Some of those entities are inert, such as warehouses, products, cartons of goods, documents and forms. Some are active, such as people and organisations. People are of especial interest. This is because they act as though they had free will; they evidence complexity in their activities, behaviours, motivations, and inconsistencies; they are the ultimate users and beneficiaries of the business that e-business performs; and they are the only means whereby organisations can act on the real world.
In order to make effective decisions within the domain of e-business, a sufficiently rich framework or meta-model is essential. Exhibit 1 depicts some of the key elements of the analysis that follows.
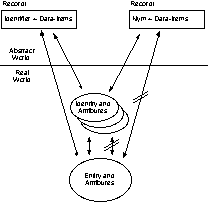
Some key aspects of the model that differentiate it from the conventional wisdom are that:
This section considers the concept of identification. The subsequent sections address authentication, and alternatives to identification.
The term entity encompasses all manner of real-world things, including objects, animals, people, and 'legal persons' such as corporations, trusts, superannuation funds, and incorporated associations. An entity has a range of characteristics, features or attributes.
This paper's focus is firstly on 'natural persons', including people performing social, economic and political functions as citizens, consumers, sole traders, and members of partnerships and unincorporated solutions; and people acting as agents both for legal persons and for other natural persons.
The second focus is on organisations. These are imaginary entities that have been invented by societies in order to mobilise resources, to share risk among multiple individuals, and to enable groups of people to sue and be sued. The law underlines the difference between organisations and people by using the term 'legal persons'.
One kind of legal person is referred to in British-derived law as a 'body politic'. This is a sovereign nation-state, or a component of a nation-state, such as a province. In many countries, most of the individual government agencies that perform the business of a body politic have no existence in law. A legal action against any such government agency is an action against the body politic as a whole.
The second category of legal person is referred to in British-derived law as a 'body corporate', and arises through an act of 'incorporation'. The primary example is the joint stock corporation / societé anonyme (SA) / Gesellschaft mit beschränkter Haftung (GmbH), the liability of whose shareholders are limited in some manner. Other examples include incorporated associations, co-operatives, strata title bodies corporate, and corporations created under specific statutes. In some countries, some kinds of bodies corporate may come into existence under the common law, in particular trusts.
A great deal of business is conducted by unincorporated enterprises, including sole traders, partnerships, joint ventures, executors, liquidators, trustees, unincorporated clubs and associations, community progress committees and cultural event committees. Such enterprises have no existence for the purposes of contract and various other laws, and no ability to sue or be sued. The parties who are deemed in law to make up the enterprise are jointly and severally liable for its acts (i.e. any one or more of them can be sued). Those parties are in most cases people, but can also be bodies corporate or even bodies politic.
Contrary to the presumptions made in many information systems, an entity does not necessarily have a single identity, but may have multiples: an identity is a particular presentation of an entity.
An organisation plays many different roles, and has many different kinds of relationship with many kinds of other organisations. Examples of these relationships include seller and buyer, supplier and receiver, debtor and creditor, payer and payee, principal and agent, franchisor and franchisee, lessor and lessee, copyright licensor and licensee, employer and employee, contractor and contractee, trustee and beneficiary, tax-assessor and tax-assessee, business licensor and licensee, plaintiff and respondent, investigator and investigatee, and prosecutor and defendant.
To reflect these varied roles, a company may have many business units, divisions, branches, trading-names, trademarks and brandnames. Similarly, bodies politic, and even individual government agencies, perform multiple roles, and may present many faces to people and to other organisations.
People also perform multiple roles, and many individuals are known by different names in different contexts. In some cases, the intention is dishonourable or criminal; but in most cases the adoption of multiple personae is neither, but rather reflects the multiple roles that people play in such contexts as their family, their workplace(s), their profession, community service and art. In common law countries, people are in no way precluded from using multiple identities or aliases. Actions that take advantage of multiple or situation-specific identities in order to cause harm or circumvent the law are, on the other hand, criminal offences.
Entities and identities exist in the real world. They are imperfectly grasped by people, and vague images of them are acquired and held in the minds of individuals. Organisations adopt a more disciplined approach to information. They actively construct models of relevant entities and identities. They do this by capturing data into data structures within information systems. In information systems:
Within an organisation's information systems, a real-world identity is operationalised as some sub-set of the data that describes it, which differentiates it from other, similar identities. For example, a car may be differentiated by its accessories, its paint-scheme, a particular pattern of dents and scratches, a particular grinding sound when changing gears, and its peculiar cornering characteristics.
More formally, an identifier is one or more data-items concerning an identity that are sufficient to distinguish it from other instances of its particular class, and that is used to signify that identity.
For a person, the set of information that makes up an identifier may be as little as a single code, specifically designed as an identifier, or may be a compound of multiple items of data, such as given and family name, date-of-birth and postcode of residence.
Identification is a process whereby an data is associated with a particular real-world identity. This is achieved by acquiring data that constitutes an identifier for it. An organisation's purpose in undertaking an identification process is to establish that an identity presenting to it is either:
The process of identification is a search for the one among many data records that corresponds to the presenting identity.
This sub-section examines ways in which the identities of humans are signified. An identifier that is used in many circumstances is the individual's name. Names are deeply rooted in history and culture, long, subject to variants, and not exclusive to an individual. Moreover, many people use names that differ from their name as it is stated on their birth certificates. Married women may use their maiden names for professional purposes and some people use their middle name instead of their first name. Pseudonyms are particularly common in certain professions, either to protect a person from potential danger, or as part of an artist's or writer's creative persona.
In most jurisdictions, especially common law jurisdictions, there are few legal compulsions relating to the use of a single name, and few legal constraints on the use of multiple names to manifest mutliple identities. The common law recognises that a name acquired 'by reputation' is a legally valid form of identification. People are, by and large, free to adopt a name as they see fit. There are advantages and disadvantages for a person in using the same name consistently over time, and a different set of advantages and disadvantages of using the same name across different roles.
The underlying principle in a free society is that citizens should be free to do as they please, and the state should only intervene to the extent necessary to prevent this freedom being exercised in a way that inhibits the freedom of others. A person can be mischievous with their identity/ies provided that they do not breach the criminal law or cause harm to someone within the bounds of tort law.
An alternative to names is multi-attribute identification. This involves several items of data being used together to recognise the person. For example, 'the person who came to the enquiry counter was female, about 150 centimetres tall, in her 50s, and had her grand-daughter with her'.
In many populations, a person may be reliably identified by a combination of their name and date of birth, perhaps supplemented by some indicator of home-address. Organisations that maintain data about people need to devise processes firstly to discover all instances of identifiers on file that are very similar to the one being provided, and secondly to overcome the ambiguities and decide which of the alternatives is the correct one. An example of this approach is the so-called 'Phonex' technique, whereby homonyms (similar-sounding names) are treated as though they were identical. This ensures that surnames commencing with 'Mac' and 'Mc' are treated as being equivalent, as are 'Clarke' and 'Clark', and 'Byrne' and 'Burn'. The resolution of ambiguities can be undertaken by bringing the relevant information to the attention of a human being, and providing to that person such additional information as may be available; or by having a computer compare additional items.
Names and multi-attributive identifiers embody significant difficulties and uncertainties. It is advantageous for organisations to contrive identifiers for the people that they deal with that can be tested for precise equality with the data held on the organisation's files. Organisation-assigned codes have the advantage of providing a relatively short and invariant string of characters, in many cases restricted to numerics, but in some cases including letters and even special characters, especially to separate a long code into segments to enhance readability.
This sub-section examines ways in which human entities are signified. Despite the fact that this is fundamentally different from the signification of mere identities, discussions about identifiers seldom distinguish the two. I suggest the term 'entifier' to refer to the signifier for an entity, and 'entification' for the process whereby an entifier for an entity is acquired.
An entifier must of necessity be some more or less formal biometric. The less formal kind comprises visual entifiers, i.e. some aspect of the person's physical appearance such as facial shape combined with the colour of hair and eyes, quite possibly supplemented by dynamic patterns such as physical mannerisms and social behaviour.
The more formal kind comprises biometric entifiers, which are measures of some aspect of a person or their behaviour. These are of several kinds:
Biometrics are generally expensive, and inconvenient to the person concerned, and demeaning to them. They also present a difficulty in that they are collected as measures rather than as fixed values. As a result, a person will seldom if ever provide a biometric that is identical to that which is already recorded. Identification involves a search for the (or a) fit between a new measure and one of many reference measures previously recorded for many people. Biometrics, by their very nature, involve variations, and tolerance margins.
Beyond their intrusiveness, biometrics have highly significant public policy implications. This is because they provide organisations and governments with power over individuals and populations, and hence threaten personal and societal freedoms, and democracy.
There are many circumstances in which it is most convenient for a business enterprise to recognise another business enterprise according to the role that it is playing. If a business entity fulfils several roles in its dealings with another business entity, it may have multiple identifiers, such as business units and business names.
In most jurisdictions, corporate names are the subject of regulation, and the sequence of letters that they are required to use is likely to be invariant (although they may in practice vary the spelling, and especially the punctuation and styling). The trading names used by business enterprises tend to be subject to less stringent and only lightly-enforced regulation. Coding schemes exist in some countries, providing a code for each legal entity. In general, business units within corporations, business names and brands do not have such registration codes.
Government agencies are generally much less reliable in their use of identifiers. In many jurisdictions there exists no reliable register of agency-names, and no registration-code.
In all cases of legal persons, there is no corporeal entity, and hence no equivalent of a biometric. In short, organisations have identifiers whose reliability varies from strong to very weak, and do not have entifiers.
Authentication is the process whereby a degree of confidence in an assertion is established. This section examines the wide variety of assertions that may be subjected to authentication.
There has been a tendency in discussions during the last few years for the term 'authentication' to be used in an unqualified manner but to refer specifically to authentication of an assertion that a person presenting to an organisation has a specified identity. This is only one kind of authentication, and it is important that the narrow term 'identity authentication' be used for it, such that the unqualified term is seen to refer to a generic concept.
The following sub-sections deal with the various categories of authentication relevant to e-business:
There are many circumstances in which organisations seek assurance that the consideration offered by a party delivers the value it purports to. In most cases, 'value' is best understood in terms of fungibility or convertibility to cash; but value may also be represented by vouchers such as certificates and tickets; and value can be imputed by the recipient of goods, services or information.
Examples of value authentication include the checking of a banknote for forgery-resistant features like metal wires or holograms, and the seeking of pre-authorisation of credit-card payments.
In a great deal of commerce, this is the key form of authentication. In e-commerce, an aberration has existed. This is because, in its few short years to date, the sole practical payment mechanism has been by means of credit cards, which carry an identifier of the cardholder. Payment mechanisms that do not have an identifier associated with them have been conceived, designed, prototyped, implemented, and trialled, but have not yet been widely adopted.
The deployment of value authentication without disclosure of identity represents a real opportunity to unlock the potential of e-commerce.
Many circumstances arise in which a message-recipient wants to authenticate an assertion that the message was originated by a particular identity. In conventional business, a range of techniques has been used to check that an act that purports to have been performed by a particular business entity actually has been. Common approaches include the expectation that communications from a business enterprise will be on authentic(-looking) letterhead, and call-back to a telephone number acquired from some other source.
The nominally highest-quality authentication of a corporation's identity and actions has been where the company's seal has been affixed to a document, and over-signed by authorised officers. This is actually of very low quality, because both the seal and the signatures are easy to spoof, and very difficult to check. With the emergence of e-commerce during the last quarter-century, the requirements for use of a company seal are in the process of being rescinded (and the requisite amendments have already been made to, for example, the Australian corporations law).
Electronic signatures in general, and digital signatures in particular, offer the prospect of higher levels of confidence. A significant difficulty that has to be addressed, however, is that, because a business entity cannot itself act, it is dependent on the actions of one or more humans acting on its behalf. In addition to the security measures needed in respect of such people's digital signature keys, further measures are needed, in order to reduce the likelihood of error or fraud through the misapplication of the organisation's own private key.
The term identity authentication refers to the process whereby an organisation establishes its degree of confidence in the particular assertion that a party it is dealing with is who they purport to be. More laboriously expressed, it is a process designed to cross-check against additional evidence the identity signified by the identifier acquired during the identification process. Authentication is expensive, and hence the degree of effort invested needs to reflect the likelihood or accidental and intentional error, and of the harm that would arise if error occurred.
One approach is to gather additional identifiers, i.e. two or more of the categories of identifier described in section 4.6 above, comprising names, multi-attribute identifiers, and codes.
A level of assurance can be established by requiring that a person demonstrate that they have some knowledge that only that person could be expected to be able to provide. In consumer and citizen counter and telephone services, for example, the person may be asked for their birthdate, their mother's or wife's maiden name, a password, or a 'personal identification number' (PIN).
Another approach is to provide the person with a token, which is some 'thing' that the person is expected to present as evidence that they are the person concerned.
Token-based schemes are very effective in tightly controlled environments, as a variant on the 'turnaround document' approach: the person first presents at a counter, then must wait in a large, anonymous area prior to visiting the counter a second time. If an identifier is issued on the first occasion, and interchange or theft of the identifier is unlikely, then its presentation on the second occasion will be fairly reliable 'proof of identity' within that limited context.
Another common form of token is a card issued by an organisation. Such cards are generally provided on the basis of documentary evidence of identity presented by the person. Examples of such documents include birth certificates, marriage certificates, passports, drivers' licences (or, in some jurisdictions, non-drivers' 'licences'), employer-issued building security cards, credit cards, club membership cards, statutory declarations, affidavits, letters of introduction, and invoices from utilities.
In the electronic arena, a form of token that might be used for identity authentication is a digital signature consistent with the public key attested to by a digital certificate.
Difficulties arise with all forms of evidence of identity. Apart from the costs and inconveniences involved, documentary evidence is fundamentally unreliable. Ultimately, all documents depend on some seed document, most commonly a birth certificate; and such documents do not embody any reliable association with an identity.
Reflecting the high degree of unreliability of each of the approaches to human identity authentication, organisations that have a need for relatively high levels of confidence commonly require one or more tokens, supplemented by knowledge-based tests. This is frequently highly inconvenient for people, often demeaning, and in many cases impractical. Corporations and government agencies commonly use their power over individuals to achieve compliance, rather than seeking consensus among stakeholders about the appropriate balance between social control and personal freedoms.
The term entity authentication refers to the process whereby an organisation establishes its degree of confidence in the particular assertion that a party it is dealing with is a specific instance of the species homo sapiens.
The entification of a human entity depends on the gathering of a biometric entifier of the person. The authentication process involves a cross-check of the entifier against a reference measure.
Authentication measures include:
Such processes are expensive, inconvenient, intrusive, and threatening. Unlike entification, however, they involve a 1-to-1 comparison between a new measure and a single previously-recorded measure. Biometric authentication is therefore capable of being designed so as to achieve balance among multiple interests, at least in principle (although seldom to date in practice).
Another approach is the authentication of attributes. This is a process whereby information about a party is checked, such as whether a person is within an age-range appropriate to some category of transaction, is a member of a particular association, or has a particular educational or other qualification. It is not the entity or identity that is in focus, but rather somethng about that entity or identity.
Attribute authentication generally involves the inspection of some kind of credential that attests to that entity or identity possessing that attribute. Many circumstances exist in which the credential identifies the person. This is not actually necessary, however. All that is needed is some means whereby the credential is reliably associated with the entity presenting the credential. For example, a series of challenges for information can be sufficient to establish that a person qualifies for entry to secure premises, without even knowing their identity let alone authenticating it.
Moreover, even where the process of attribute authentication involves the provision of an entifier or identifier, there may be no need to record anything more than the fact that authentication was performed. In this way, the transaction ceases to be identified. An example of this is the inspection of photo-id, without recording the identifier displayed on the card.
A special case of attribute authentication, and one highly relevant to e-business, is the authentication of an assertion that an entity has the legal capacity to formally represent another entity, and to bind them in contract. The representative is referred to as an agent, and the party being represented is called the principal.
Agents may be appointed to act on behalf of people, or of bodies corporate. It is common to evidence the relationship by means of a document generally referred to as a power of attorney. Organisations are legal fictions that have served advanced economies very well, and continue to do so. They cannot, however, act directly on the real world, and hence some natural person must do things on their behalf.
In many cases, there is a chain of agency relationships, passing through multiple organisations and individuals. An example is an employee of a customs agency, which is acting on behalf of another customs agency that operates in a location overseas, which in turn acts for an exporter. A chain of three principal-agent relationships among bodies corporate culminate in a principal-agent relationship between the last company and its employee. In principle, the authentication of an agent requires inspection and testing of the evidence for the complete series of delegations. In practice, such inspections and testing are very rarely performed, and in most cases they would be impractical anyway. Society runs on a great deal of trust.
To date, agents have always been human. There is an increasing number of examples of acts delegated to artificial intelligences, however, through such means as automated telephone, fax and email response; automated re-ordering; program trading; and other forms of software agent. Legislatures and courts may be becoming willing to accept these acts as being binding on the entity concerned, at least under some circumstances.
The identification and authentication schemes operated by business enterprises must be sufficiently sophisticated to distinguish between the acts and identities of principals, of intermediate agents, and of ultimate agents. Care is needed to ensure not only that the relationship between principal and agent exists at the relevant time, but also that it actually encompasses the kind of transaction being conducted, and does not exceed any limitations on the agent's power to act on behalf of, and bind, the principal. A further complication is that an agent may act for multiple principals, and a principal may be represented by multiple agents. This results in multiple credentials, and scope for conflicts of interest to arise that need to be managed.
Analogous arrangements have been envisaged for the electronic context, applying cryptographic techniques. One approach that might be used is to authenticate the identity of the individual and/or business entity (as discussed in the preceding sub-sections), and then check some kind of register of identities authorised to act on behalf of the relevant business entity. The register might even be implemented in distributed fashion, by setting an indicator within the person's own signature chip-card.
Another approach is direct authentication of an authorisation. For example, a business entity's private key could be used to digitally sign a particular kind of instrument, which a recipient could confirm (using the business entity's widely available public key). This would be a more direct mechanism, and would avoid unnecessary declaration and authentication of the identity of the agent. It would, on the other hand, involve risk of appropriation or theft of what amounts to a bearer instrument.
The nature of identification and entification processes is such that authentication is never perfect, but rather is more or less reliable. This section considers key factors relevant to the quality of those processes.
There are many desirable characteristics of an identifier if it is to provide the basis for a reliable identification scheme. Adapting a longstanding set of criteria proposed decades ago by an information technology provider, these include:
Clearly, many of these suit organisations very well, but are inconvenient, objectionable, and even downright obnoxious from the standpoint of an individual whose identifier is being acquired and authenticated. The problem is even more acute where the criteria are applied to entifiers, and hence to individual's own bodies. A serious tension exists between the needs of organisations and the interests of individuals.
Identifiers and entifiers for people present enormous challenges, and most are of low quality when assessed against the above criteria. Those for bodies corporate and agencies within bodies politic are also seriously problematical.
A range of risk factors impinge on quality. Of especial importance is the need to achieve an appropriate balance between the harm arising from:
Sources of poor quality include the following:
Where quality shortfalls occur, additional considerations that come into play include the following:
The approach most commonly used in the context of e-business is a string of characters (a loginid) as identifier, and an additional string of characters (a password) as a means of using the person's knowledge as an authenticator. Many risks exist, which are partially addressed through such technical measures as channel encryption (in particular SSL/TLS), Kerberos, and one-time password schemes. A further approach is e-tokens that use public key cryptography. This is fraught with problems, and is addressed in a companion paper.
The level of assurance or strength of anauthentication mechanism depends on the extent of protections against abuse (such as avoidance, subversion or spoofing/masquerading), and hence whether it can be effectively repudiated by the entity concerned. It is useful to distinguish the following levels of authentication:
Where an authentication process results in a very high degree of confidence in an assertion, the term 'verification' may be appropriate. In most circumstances, however, achieving strong authentication is very difficult and/or very expensive and/or highly intrusive. Where the process results in less than strong authentication, the degree of confidence that can be attained is too low to justify such a strong expression as verification. Strong authentication is associated with the concept of 'absolute trust', which has currency in some military and national security applications. Business enterprises and most government agencies generally adopt a 'risk management' approaches, which rely on lower levels of assurance, but are cheaper, more practical, easier to implement and use, and less privacy-invasive.
Some individuals are unable to provide the identifiers, entifiers or authenticators that organisations demand from them. For example, some people have an awkward name, no documents, a poor memory, no thumb, or provide biometrics that are statistical outliers and frequently result in false negatives. These people suffer the consequences, such as repeated delays in their dealings with organisations, and suspicion at checkpoints.
A more general consideration is the extent to which organisations exercise power over individuals by imposing technology on them, and signify their power through repetitively forcing people to submit. Public resentment and suspicion result in the active use of countermeasures of various kinds, not only by miscreants and criminals, but also by the general public. This reduces the effectiveness of the schemes employed.
High-reliability authentication processes are generally costly to all parties concerned, in terms of monetary value, time, convenience and intrusiveness. Many other factors need to be considered in addition to the degree of confidence that the identifier and authentication processes are capable of generating. These include the practicality, the cost (not only in direct financial terms, but also in the time of both the organisation's employees and affected individuals), and the extent to which the technique and process are acceptable by the public, and by people with particular cultural interests, including those of specific language groups, religions and denominations, and aboriginal groups.
Organisations therefore generally implement an approach that represents a trade-off between quality and the many other factors relevant in their particular context. The particular evidence used in authentication varies a great deal depending on the purpose of the transaction, and the context in which it is being undertaken.
The presumption is often made that transactions and relationships should generally be identified. This section tests that presumption and investigates the alternative approaches of anonymity and pseudonymity.
There are many circumstances in which transactions are conducted between individuals and organisations without any identifying data being made available by the person concerned. Examples include telephone and counter enquiries by members of the public, the collection of brochures from stands, and (with qualifications) visits to web-sites. Such interactions are often two-sided anonymous, in that the member of the public is aware of the identity of the agency they are dealing with, but not of the individual employee or contractor with whom they are communicating.
There is a variety of circumstances in which an organisation does have a need for the identity of the person. This is because some categories of transactions are difficult to conduct on an anonymous basis, without one or perhaps both of the parties being known to the other. Examples of transactions where an argument for identification may be tenable include:
More generally, circumstances in which identification may matter are the following:
Even in some of these circumstances, however, designs, prototypes and even operational schemes exist, that enable protection of the parties' interests without disclosure of the person's identity. An example is credit-card schemes, which are entirely feasible without direct identification of the card-owner.
Viewing the matter from the opposite perspective, there are factors that constrain a person's freedom to use whatever identifier they like. They include the following;
An anonymous transaction is one in which no identity is associated with the data. There is a vast range of transactions for which identification is not a logical prerequisite. These include:
People desire anonymity for a variety of reasons. Some of these are of dubious social value, such as avoiding detection of their whereabouts in order to escape responsibilities such as paying debts and supporting the children of a broken marriage; avoiding retribution for financial fraud; and obscuring the flow of funds arising from illegal activities such as theft, drug-trading and extortion (commonly referred to as 'money-laundering').
Other reasons for seeking anonymity are of arguably significant social value. Examples include:
It is often blithely assumed that the interests of parties to a transaction cannot be protected if the transaction is conducted anonymously. This assumption is sometimes correct, but not always so. In many situations anonymous transactions are perfectly permissible, as long as they do not hurt anyone in a way that falls within the sphere of criminal fraud or negligent misrepresentation, or are specifically prohibited by legislation. For example, virtually all cash transactions are anonymous, whether by accident or by design. Anonymity remains one of the most effective responses to threats to personal privacy.
The concern is frequently expressed that anonymity compromises accountability, in that it undermines society's ability to impose sanctions on criminals and miscreants, and therefore reduces the extent to which fear of retribution curbs disapproved behaviour.
Nonetheless, anonymity is a natural state, and may well remain so, despite the ravages that have been wrought by technologies, particularly during the last few decades. Moreover, in the context of e-business, a substantial industry is emerging, whose purpose is to enable and assure the ability to communicate and act in cyberspace without an identifier, still less an entifier, being associated with the resulting data.
Between the two extremes of identified and anonymous transactions is the concept of a pseudonymous transaction. This is one in which a pseudo-identifier or pseudonym is associated with the data.
A pseudonymous record or transaction is one that cannot, in the normal course of events, be associated with a particular individual. Hence a transaction is pseudonymous in relation to a particular party if the transaction data contains no direct identifier for that party, and can only be related to them in the event that a very specific piece of additional data is associated with it. The data may, however, be indirectly associated with the person, if particular procedures are followed, e.g. the issuing of a search warrant or other form of court order, authorising override of the protections.
Nyms are used by criminals. They are also used by many other, much more interesting people, and are an important part of the rich fabric of human culture. A common application of pseudonymity is to reflect the various roles that people play. For example, on any one day, a person may act as their private selves, as an employee of an organisation, as an officer of a professional association, and as an officer of a community organisation. In addition, a person may have multiple organisational roles (e.g. substantive position, acting position, various roles on projects and cross-organisational committees, bank signatory, first-aid officer and fire warden), and multiple personal roles (e.g. parent, child and spouse; scoutmaster, sporting team-coach and participant in professional and community committees; writer of letters-to-the-newspaper-editor and participant in newsgroups, e-lists and chat-channels; chess-player, on-line game-player, and user of on-line gaming services).
The simplest way to implement a pseudonymous scheme is to maintain an index that correlates the pseudo-identifier with an identifer or entifier. The concept, usefully referred to as 'identity escrow', involves these elements:
The relationship between the pseudonym and the actual person or organisation may be unauthenticated, or weakly, moderately, or strongly authenticated.
The trusted third party must maintain a cross-index between the indirect identifier and the real identifier. It must apply appropriate technical and organisational security measures, and divulge the link only in circumstances specified under legal authority, such as contract, legislation, search warrant or court order.
Such mechanisms already exist in a variety of settings, such as the following:
The first of the above examples, banking secrecy, has been significantly reduced in recent years, because of the extent to which it has been used to hide the proceeds of crime. It would be a mistake, however, to assume that this demonstrates that pseudonymous banking is unjustifiable. The original intention of Swiss banking secrecy was the protection of Jews who broke German law in the 1930s by depositing value in Swiss banks. During the second half of the twentieth century, the technique was applied to less worthy purposes, without any adjustment to the checks and balances within the system. The need is for both identity-protection methods, and the means to override the protections when the public interest demands it.
Identified transactions use an identifier or entifier for the person concerned. A word is needed for the equivalent concept where the transaction is anonymous or pseudonymous.
How mainstream the concept is is evidenced by the wide range of terms that are available to choose from. They include aka (short for 'also-known-as'), alias, avatar, handle, nickname, nick, nom de guerre, nom de plume, moniker, persona, personality, profile, pseudonym, pseudo-identifier, sobriquet, and stage-name. The author coined the term 'digital persona' in 1994 to refer to "a model of an individual's public personality, based on data, maintained by transactions, and intended for use as a proxy for the individual". At about the same time, the term 'e-pers' (an abbreviation of electronic persona) was suggested. These terms almost all have particular usages and connotations, and they evidence somewhat different meanings. The term 'nym' appears to be gaining currency, and has the advantages of being derived from a relevant Greek root, and carrying no semantic baggage with it.
A 'nym' is one or more data-items relating to an identity that are sufficient to distinguish it from other instances of its particular class, but without enabling association with a specific identity or entity. For example, an email-address such as hotdoggity@hotmail.com, enables an organisation to conduct not just one transaction, but also multiple transactions over a series of episodes, and even enables the individual and the organisation to establish a relationship, without the organisation knowing who the person is that is using that nym.
Most commonly, there is a 1-to-n relationship between a person and nyms, i.e. each person uses zero, one or more nyms, and no-one else uses those nyms. Other arrangements are also possible. however. A nym can be used on a 1-to-1 basis, i.e. precisely one person can use that nym, and no other nym. Alternatively, nyms can be used on an n-to-1 basis, i.e. many people use the same nym. An example of such a usage is within organisations where a common email account is used for a particular function, such as webmaster@<organisation>.org.<cc>, sales@<corporation>.com.<cc>, and enquiries@<agency>.gov.<cc>.
A common application of nyms is where a person establishes multiple relationships with the same organisation, with a separate nym for each relationship. This may be to reflect the various roles the person plays when it interacts with that organisation (e.g. contractor, beneficiary, share-holder, customer, lobbyist, debtor, creditor). For example, an employee of a driver-licensing registry who themselves holds a driver's licence is likely to have a licence-number different from their employee-number.
A further function of a nym is to put at rest the minds of people who are highly nervous about the power of organisations to bring pressure to bear on them. Examples of relationships for which nymity is critical include socially sensitive treatments such as sexually-transmitted diseases and substance-dependence, 'whistle-blowing', police informers, and national security operatives.
One-time nyms are of limited use. For example, a person can make up a name when they call an enquiry service; but if they call again and want to continue the conversation with the enquiry service where they left off, then they will be unable to do so without using the same made-up name. This is because the organisation is unable to recover the previous data from its database unless an identifier is available.
There are therefore some additional features that nyms need to have if they are to support transactions of any complexity, or long-term relationships. These include:
An increasing array of technologies exist that enable nyms. In the contemporary contexts of highly data-intensive relationships, and Internet-mediated communications, pseudonymity and multiple nyms are especially important measures to encourage the adoption of all forms of e-business.
This document has presented a model of identification and authentication. It has argued that the design of e-business services have been founded on an excessively simplistic understanding of the concepts, and that these inadequacies have been significant factors in the lack of public trust in all forms of e-business and in the resultant low adoption rates. Progress will only be possible if attention is paid to the subtleties.
A first important requirement is that the distinction needs to be appreciated between identities and entities, and hence between the signifiers of each, and the processes whereby signifiers are acquired.
Processes to acquire signifiers of entities, dependent as they are on biometrics, are gross intrusions on individuals. Moreover, the risk of biometric masquerade, and hence identity theft, is very high in the e-business context. Biometric measures of humans should therefore only be imposed in circumstances in which their use is clearly justified, alternative measures have been expressly considered and found wanting, and effective protections against escape of the biometrics have been built in.
The existence and tenability of anonymity must be recognised. Anonymous payment mechanisms such as Chaumian eCash need to be deployed. Of especial importance is the development of techniques for the authentication of attributes without the disclosure of identity.
Anonymity, while not entirely precluding accountability, certainly compromises it. Pseudonymity offers a way to achieve balance between privacy and accountability. Progress in this area depends, however, on recognition of the need, credible legal protections, and the development and deployment of technologies to support it.
Particularly to encourage reliable business dealings among corporations, it is also vital that attribute certificates be developed in such a manner that principal-agent relationships can be communicated and authenticated.
These requirements underline the inadequacies of conventional public key infrastructure designs, and imply the need to re-think and re-engineer PKI from the ground up, removing the fixities, overcoming the limitations, abandoning the flawed concept of certification authorities, and substituting risk management approaches for the myth of CA-based assurance.
CACM (1999) 'Internet Privacy: The Quest for Anonymity' Special Section of Commun. ACM 42, 2 (February 1999), at http://www.research.att.com/~lorrie/pubs/cacm-privacy.html
Clarke R. (1994a) 'The Digital Persona and its Application to Data Surveillance', The Information Society 10, 2 (June 1994)', at http://www.rogerclarke.com/DV/DigPersona.html
Clarke R. (1994b) 'Human Identification in Information Systems: Management Challenges and Public Policy Issues', Information Technology & People 7,4 (December 1994) 6-37, at http://www.rogerclarke.com/DV/HumanID.html
Clarke R. (1995) 'When Do They Need to Know 'Whodunnit?' The Justification for Transaction Identification: The Scope for Transaction Anonymity and Pseudonymity' Proc. Conf. Computers, Freedom & Privacy, San Francisco, 31 March 1995, at http://www.rogerclarke.com/DV/PaperCFP95.html
Clarke R. (1996) 'Identification, Anonymity and Pseudonymity in Consumer Transactions: A Vital Systems Design and Public Policy Issue' Proc. Conf. 'Smart Cards: The Issues', Sydney, 18 October 1996, at http://www.rogerclarke.com/DV/AnonPsPol.html
Clarke R. (1997) 'Chip-Based ID: Promise and Peril' Proc. Int'l Conf. on Privacy, Montreal, 23-26 September 1997, at http://www.rogerclarke.com/DV/IDCards97.html
Clarke R. (1998) 'Public Key Infrastructure: Position Statement', May 1998, at http://www.rogerclarke.com/DV/PKIPosn.html
Clarke R. (1999a) 'Internet Privacy Concerns Confirm the Case for Intervention' Commun. ACM 42, 2 (February 1999) 60-67, at http://www.rogerclarke.com/DV/CACM99.html
Clarke R. (1999b) 'Identified, Anonymous and Pseudonymous Transactions: The Spectrum of Choice' Proc. User Identification & Privacy Protection Conf., Stockholm, 14-15 June 1999, at http://www.rogerclarke.com/DV/UIPP99.html
Clarke R. (2000) 'Privacy Requirements of Public Key Infrastructure' Internet Law Bulletin 3, 1 (April 2000) 2-6. Republished in 'Global Electronic Commerce', published by the World Markets Research Centre in collaboration with the UN/ECE's e-Commerce Forum on 'Electronic Commerce for Transition Economies in the Digital Age', 19-20 June 2000, at http://www.rogerclarke.com/DV/PKI2000.html
Clarke R. (2001a) 'Biometrics and Privacy' 15 April 2001, at http://www.rogerclarke.com/DV/Biometrics.html
Clarke R. (2001b) 'The Fundamental Inadequacies of Conventional Public Key Infrastructure' Proc. Conf. ECIS'2001, Bled, Slovenia, 27-29 June 2001, at http://www.rogerclarke.com/II/ECIS2001.html
Clarke R. (2001c) 'Trust in the Context of e-Business' 1 October 2001, at http://www.rogerclarke.com/EC/Trust.html
Clarke R., Dempsey G., Ooi C.N. & O'Connor R.F. (1998a) `Technological Aspects of Internet Crime Prevention', Proc. Conf. 'Internet Crime', Australian Institute for Criminology, Melbourne University, 16-17 February 1998, at http://www.rogerclarke.com/II/ICrimPrev.html
Clarke R., Dempsey G., Ooi C.N. & O'Connor R.F. (1998b) `The Technical Feasibility of Regulating Gambling on the Internet', Proc. Conf. 'Gambling, Technology & Society: Regulatory Challenges for the 21st Century', Rex Hotel Sydney, Potts Point, 7 - 8 May 1998, Australian Institute for Criminology, Melbourne University, at http://www.rogerclarke.com/II/ICrimPrev.html
Clarke R., Dempsey G., Ooi C.N. & O'Connor R.F. (1998c) 'A Primer on Internet Technology', at http://www.rogerclarke.com/II/IPrimer.html
Ehrlich T. (1966) 'Passports' 19 Stanford L. Rev. 129-149 (1966-67)
EPIC (1997-) 'EPIC Online Guide to Practical Privacy Tools', at http://www.epic.org/privacy/tools.html
FACFI (1976) 'The Criminal Use of False Identification: the Report of the Federal Advisory Committee on False Identification', U.S. Dept of Justice, 1976
Fox-Davies A.C. & Carlyon-Britton P.W.P. (1906) 'A Treatise on the Law Concerning Names and Changes of Name' Elliot Stock, London, 1906
Froomkin A.M. (1995) 'Anonymity and Its Enmities' 1995 J. Online L., at http://www.law.cornell.edu/jol/froomkin.htm
Greenleaf G.W. & Clarke R. (1997) 'Privacy Implications of Digital Signatures', Proc. IBC Conference on Digital Signatures, Sydney, March 1997, at http://www.rogerclarke.com/DV/DigSig.html
Josling J.F. (1980) 'Change of Name' Oyez Publishing, London, 1st Edition, 1946, 12th Edition, 1980
Lampson B., Abadi M., Burrows M. & Wobber E. (1992) 'Authentication in distributed systems: theory and practice' ACM Transactions on Computer Systems, 10(4):265-310, November 1992, at http://gatekeeper.dec.com/pub/DEC/SRC/research-reports/abstracts/src-rr-083.html
McCullagh D. (1998-) 'Nym Resources', at http://www.well.com/user/declan/nym/
Moenssens A.A. (1969) 'Fingerprints and The Law' Chilton, Philadelphia, 1969
Neumann P.G. (1996) 'Risks of Anonymity' Insider Risks Column, Commun. ACM 39, 12 (December 1996)
Sneddon M. (2000) ,Legal Liability and e-Transactions` National Electronic Authentication Council, Canberra, Australia, August 2000, at http://www.noie.gov.au/publications/NOIE/NEAC/publication_utz1508.pdf
Turack D.C. (1972) 'The Passport in International Law' D.C. Heath & Co., Lexington MA, 1972
TIS (1994) Special Issue of Information Technology & People 7, 4 (1994) on 'Identification Technologies'. Preface at http://weber.ucsd.edu/~pagre/identification.html
Wilton G.W. (1938) 'Fingerprints: History, Law and Romance' William Hodge & Co., London, 1938
Winn J.K. (1998) 'Open Systems, Free Markets,and Regulation of Internet Commerce' 72 Tulane L. Rev. 1177 (1998), at http://www.smu.edu/~jwinn/esig.html
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in the Cyberspace Law & Policy Centre at the University of N.S.W., a Visiting Professor in the E-Commerce Programme at the University of Hong Kong, and a Visiting Professor in the Department of Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 5 October 2001 - Last Amended: 19 October 2001 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/EC/AuthModel011019.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy